Gmail OAuth Phishing Goes Viral
On Wednesday, a Gmail phishing attack leveraging OAuth spread quickly to multiple users. There are a number of features that you need to be aware of that made this attack incredibly successful, as well as ways to protect yourself or your employees that are detailed below.
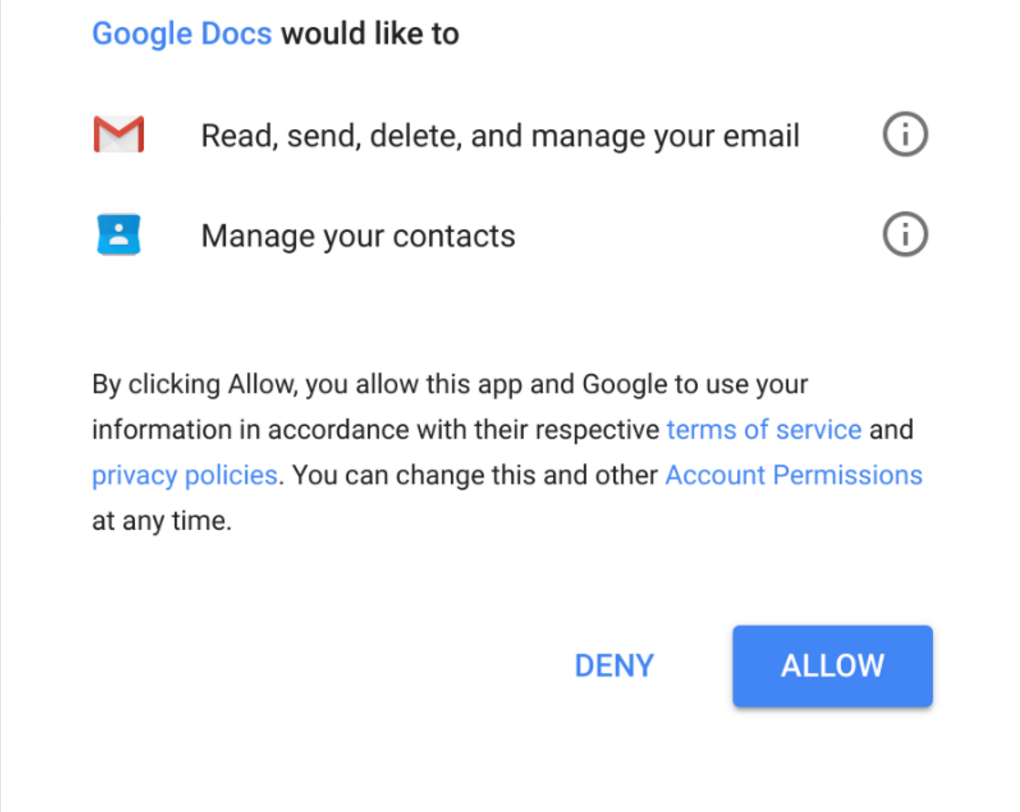
What Made This Attack Different?
This attack started with a phishing email that originated from someone the recipient likely knew. The email purported to be a request to share a document via Google Docs.
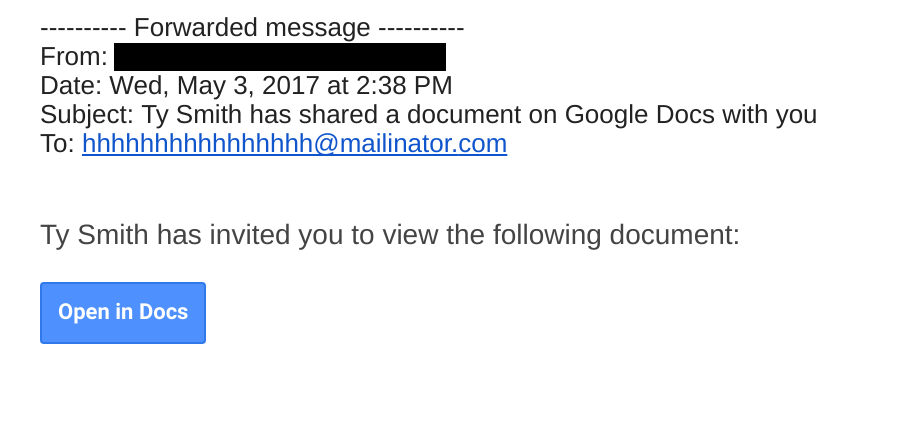
Normally, phishing attacks will then present a fake login page that attempts to trick users into submitting their username and password. These credentials are then sent to the attacker and used to gain access to the email account.
This attack was different in that once the user clicks the “Open in Docs” button, they are taken to a page which requests OAuth permissions for their account, allowing the attacker to hijack the Gmail account to send email on the user’s behalf without needing their credentials. Before going into details, it’s worth a quick background on why OAuth can make for effective phishing campaigns.
OAuth Can Be Convincing
OAuth allows third-party applications to access a service on your behalf without needing your credentials. Instead, the application will request certain permissions depending on what parts of the service it needs to access. This is a legitimate way to safely give applications limited access to a service as your account without giving up your credentials.
This attack used OAuth to gain access to manage contacts and email for the user’s Google account. This allowed it to harvest new recipients, send the emails as the victim to those recipients, and then delete the emails from the user’s Sent Mail.

There are multiple elements to this campaign that made it highly effective:
- The email was sent to a user’s contacts, which means recipients saw the email coming from someone they likely know
- The email looks like a legitimate Google Docs request to share a document
- The malicious third-party application was named “Google Docs,” matching the email pretext and appears legitimate to many users (it’s unclear if Google will prevent applications from being named like this in the future)
- Using OAuth meant that the user was never prompted to enter their credentials, only to allow access to an application. This means the user is already logged into their Google account, mitigating strong passwords or two-factor authentication (2FA).
Worm-Like Behavior
This attack went viral in minutes due to its convincing nature and the way it spread to other recipients. For each new victim, the attack spread to all of their contacts which could lead to exponential growth similar to that of other computer worms, such as the “ILOVEYOU” worm.
Since this is a malicious third-party application gaining access to an account via OAuth, the application could use Google’s APIs to automate a majority of the attack, spreading the attack even more easily and quickly.
This Isn’t Just Email
It’s important to note that OAuth isn’t just supported by Gmail. Many service providers such as social networks support OAuth as a means to allow applications to access specific resources on behalf of users. It’s no stretch to say that this same type of attack abusing OAuth permissions could be effective on other services as well.
How to Protect Yourself
Click Carefully
OAuth phishing isn’t going away. The success of this campaign suggests that we are likely to see more of this type of phishing moving forward. These attacks are easy to automate, are cheap to set up, and, as we saw on Wednesday, are very effective.
The first step for protecting yourself against this type of phishing scam is to be careful which links you click on in emails. These emails all had the recipient listed as a “mailinator” address (a disposable email service), with the actual recipient BCC’d. This could be a hint that the email may not be legitimate.
The next step to protecting yourself from OAuth phishing attacks is to be careful which applications you let access your account. When you encounter a new application request, review the permissions to determine if you’re ok with letting the app have access to those parts of your account. A good tip is to be as careful with OAuth permissions as you are with your actual credentials.
You can also review information about the developer of the application to help determine if it might be malicious. By clicking the application name (in this case, “Google Docs”), you can see the following:
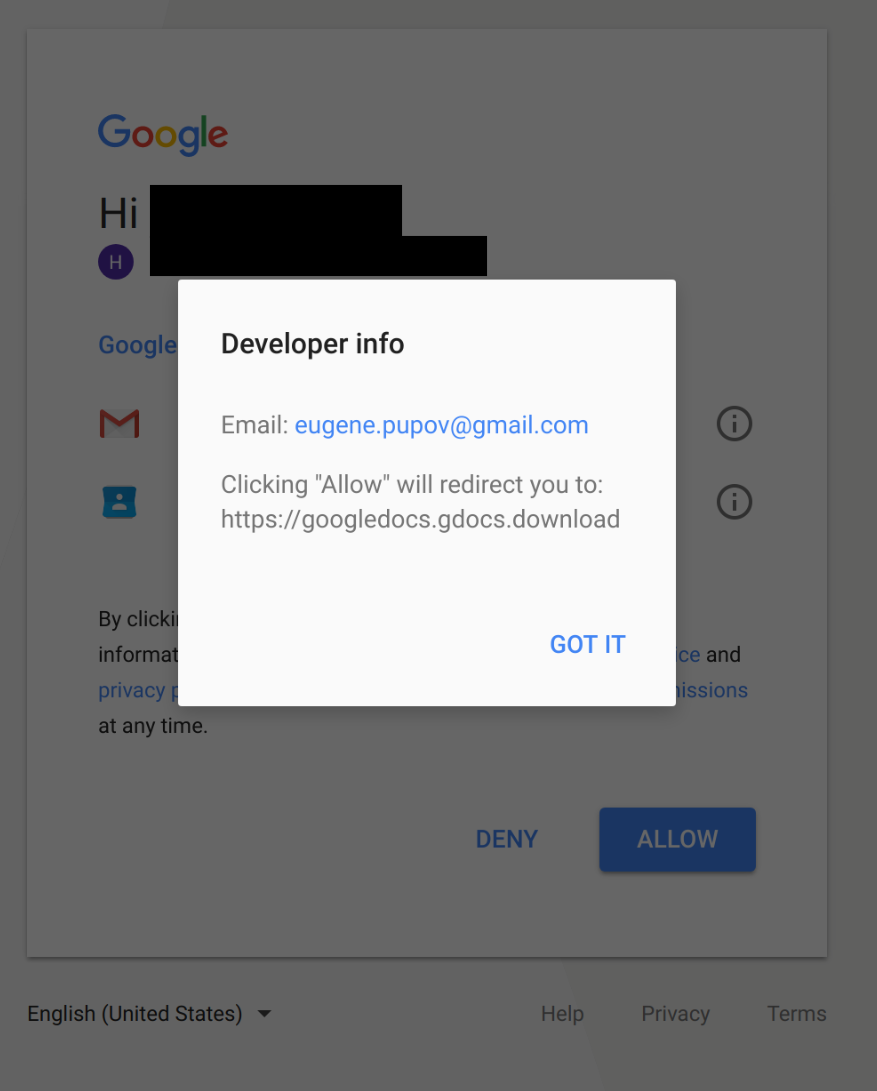
In this case, the email address for the developer appears to be a non-official personal Gmail account.
Also, as part of the OAuth process, you are redirected back to the third-party application when you allow access. In this case, you are redirected back to a URL that tries to look legitimate, but is not an actual URL operated by Google.
Review Existing Applications
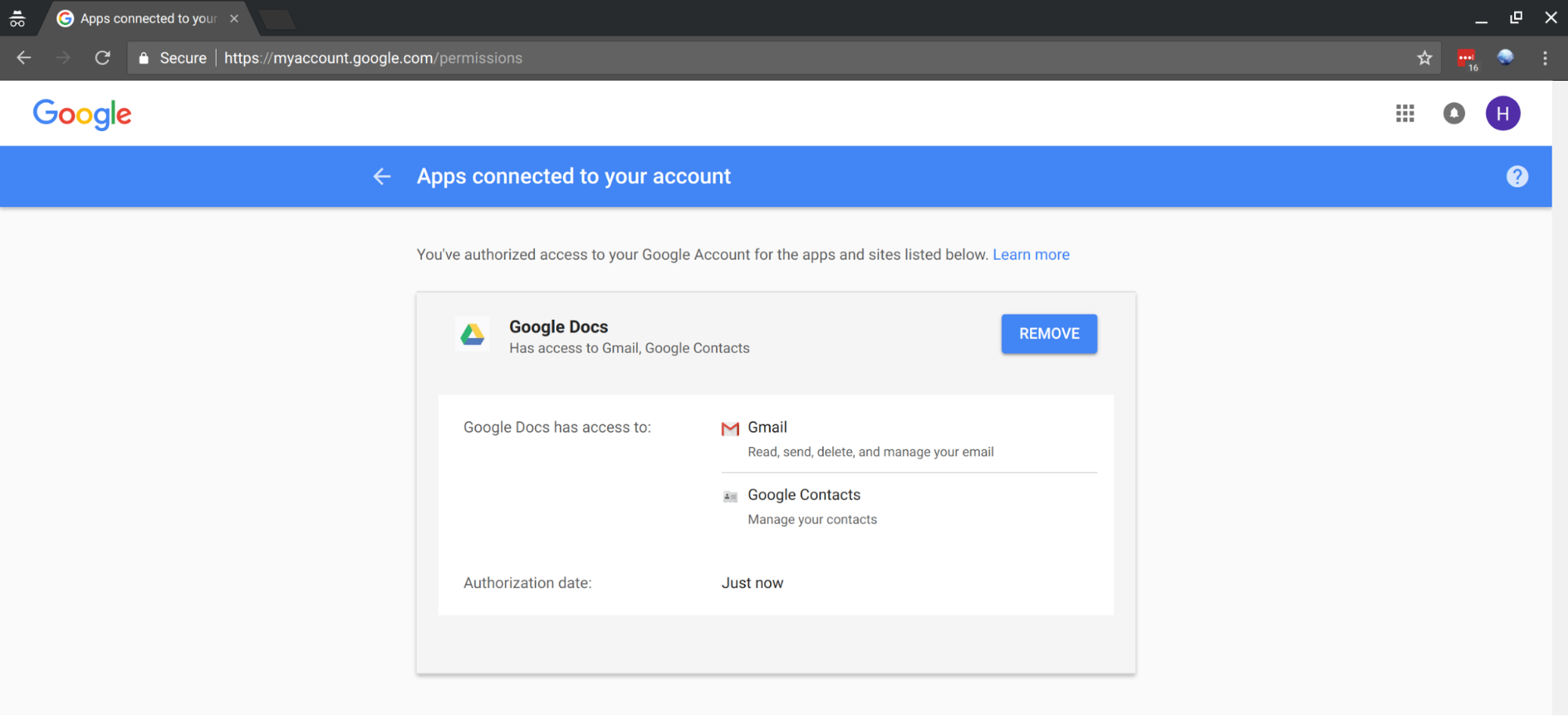
This is a good time to review what applications have access to your Google account. Over time, you may have given permission to applications that you no longer use. However, those applications can still have access to your Google account unless you explicitly revoke their access.
You can review which applications have access to your Google account (and revoke that access) by going to https://myaccount.google.com/permissions.
In this case, if you allowed the fake “Google Docs” application to access your Google account, you can revoke it by going to the permissions page, finding the “Google Docs” entry and clicking “Remove:”
Conclusion
This attack was a great example of how powerful OAuth phishing can be. However, while this event spread rapidly, the great work from service providers like Google and Cloudflare to shut down the attacker’s infrastructure helped rein in the attack just as quickly as it began.
As OAuth phishing becomes more common, it’s important to be careful when letting new applications access your account, as well as regularly reviewing which applications still have access.
To assess your organization’s risk of getting phished, launch an internal phishing campaign using our free phishing tool, Duo Insight.

