Identity Threat Trends for Higher Education
As a new semester begins, we at Cisco Duo want to share some findings and trends pertaining to threat activity we have seen across higher education customers. We will outline the trends and attack patterns that are the most prevalent and discuss how to configure Duo policies to best protect your users.
What happened?
In analyzing de-identified customer data over the latter half of 2023, we found a pattern of threat activity targeting multiple universities using shared attack infrastructure. The attack methods included a mixture of passcode phishing and push harassment, with the intent to access university VPNs or register a malicious authentication device on one or more user accounts for continued access.
Threat vectors discussed:
Passcode Phishing: An attacker uses a fake website to collect a one-time passcode from a user, which they can then use to authenticate
MFA Fatigue: An attacker sends repeated Push requests to a user, in the hopes that the user will mistake a request for a legitimate authentication or approve it to stop the flood of requests
Device Registration: After an attacker gains access to a user account, they register their own MFA device so that they can continue to access the account in the future
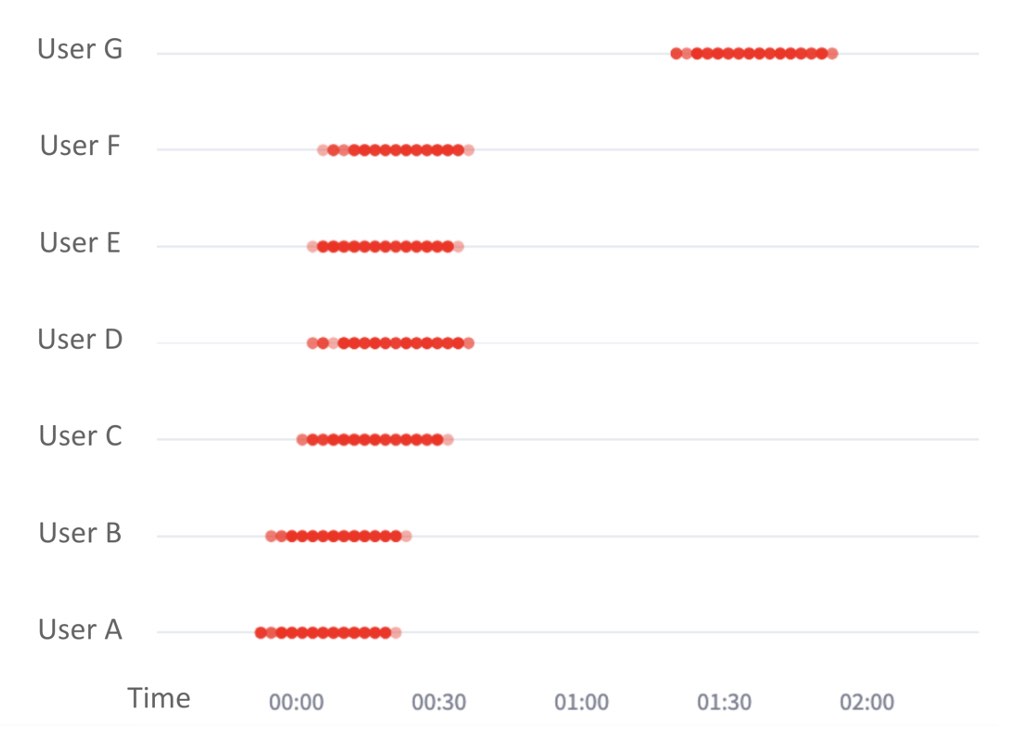
For example, here we can see a sequence of failed authentications, represented by red dots, as the attacker crawls across multiple users at an organization. In this situation, we can assume that they have either phished users’ first factor credentials (their password), or are crawling user accounts with weak, guessable passwords. The attacker sends a flurry of Push requests to each user, in the hopes that a user will inadvertently grant access. In this example, the users thankfully did not respond to the attacker’s requests, but this isn’t always the case.
How did Duo investigate and respond?
These attack patterns were initially identified via notifications from concerned customers. We knew we needed to do more to investigate the attack and provide support to customers, so we collaborated with Cisco Talos to hunt for and respond to additional activity. As malicious infrastructure was identified throughout this research, we blocked it from accessing our systems, and took steps to notify customers that were impacted. Also, the patterns seen here were cataloged for further development of threat detection mechanisms that will enhance our customers' security.
What can Duo customers do to protect themselves?
The activity observed in these attacks represents some of the most common attack patterns against MFA. Duo customers in the educational sector and beyond can take steps to secure their environments.
Credential Rotation
While security professionals do not recommend that organizations force users to regularly change their passwords, compromised passwords should always be changed. Even if access was not ultimately gained, any malicious MFA attempts typically signify a breach of first factor credentials. Administrators should take care to monitor for unusual patterns of failed login activity and encourage affected users to set new strong, unique passwords.
More Secure Authentication Factors
If you haven’t already, consider securing your user Device Management Portal to only allow more secure authentication factors, such as Verified Duo Push or WebAuthn authentication methods.
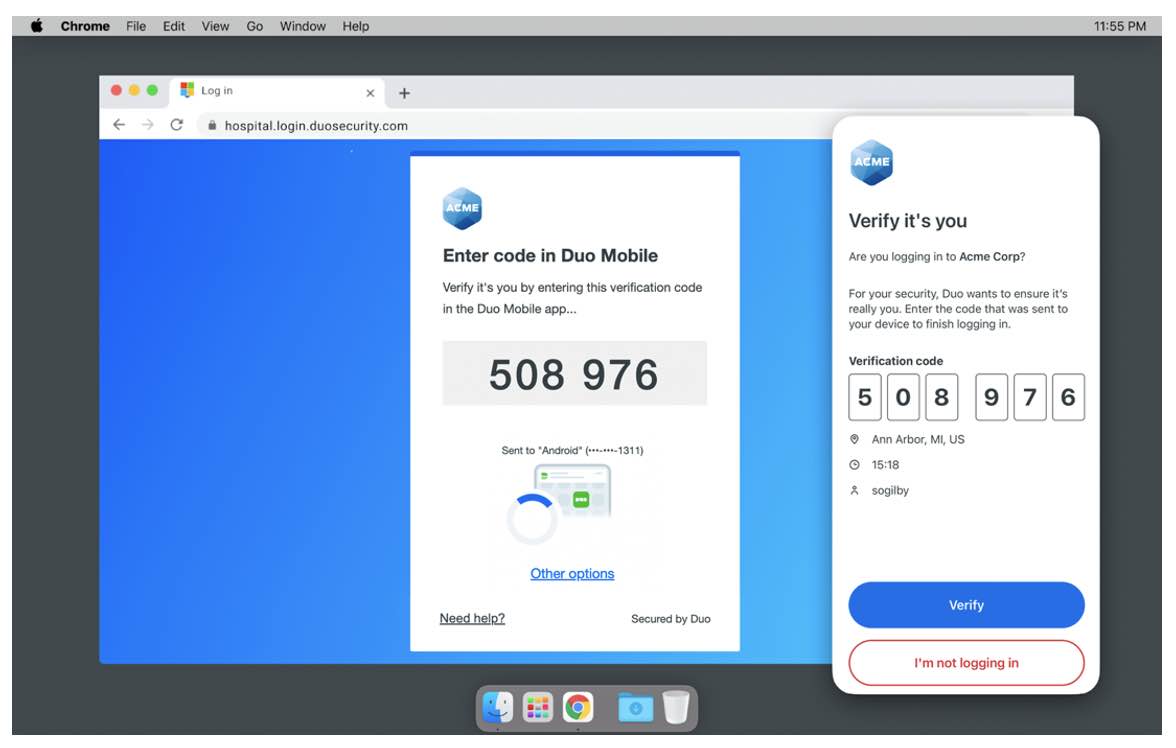
Additionally, Duo’s Risk-Based Authentication (RBA, available on Premier and Advantage editions) can intelligently force a “step-up” to require a more secure factor like Verified Duo Push when an attack pattern, like push harassment, is detected. In the context of the attack shown in the previous section, after multiple failed authentications the attacker would be disabled from making further Push attempts. If the attacker selected a different factor like Verified Duo Push, the trusted user would not have the code provided on the access device, and could not inadvertently approve the authentication.
Duo Trusted Endpoints
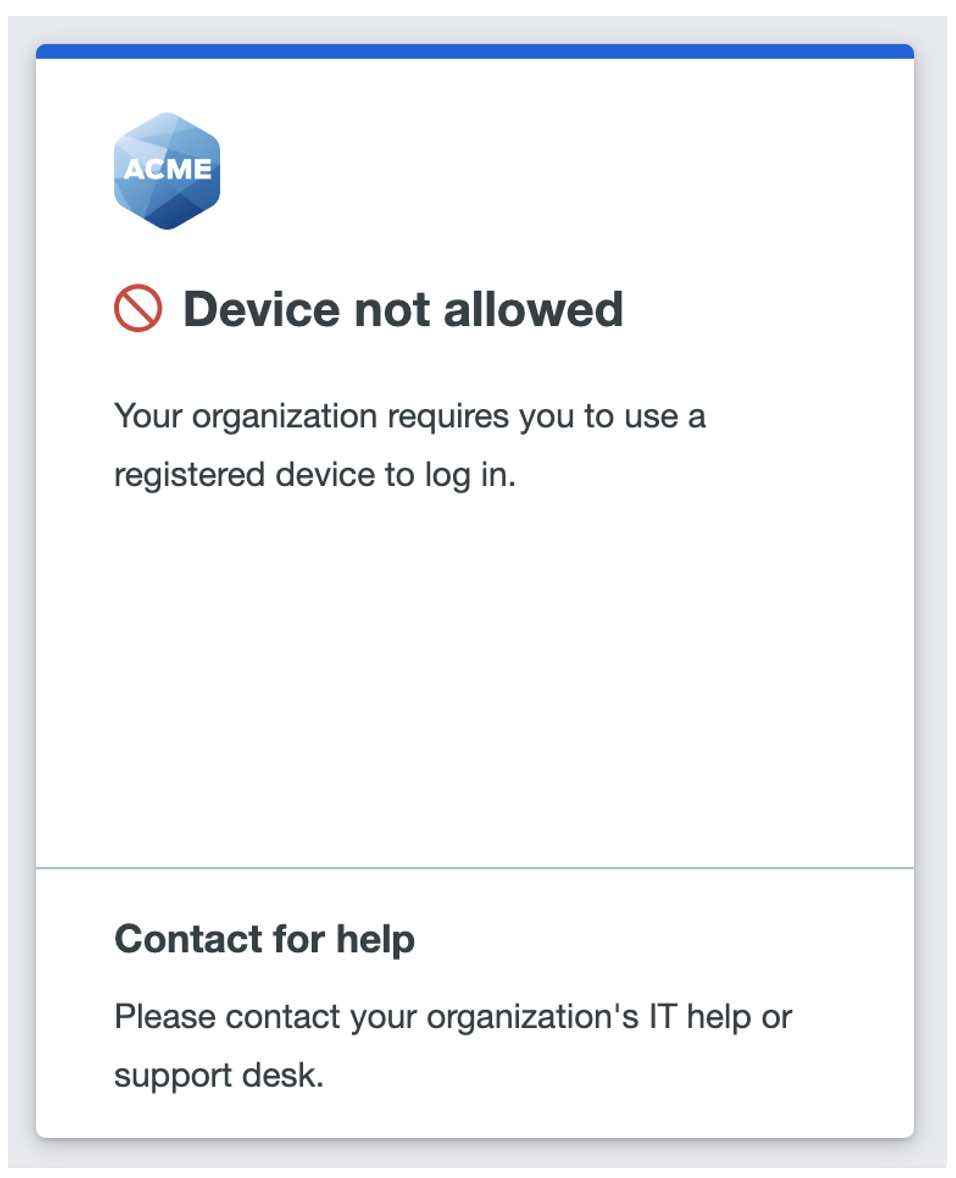
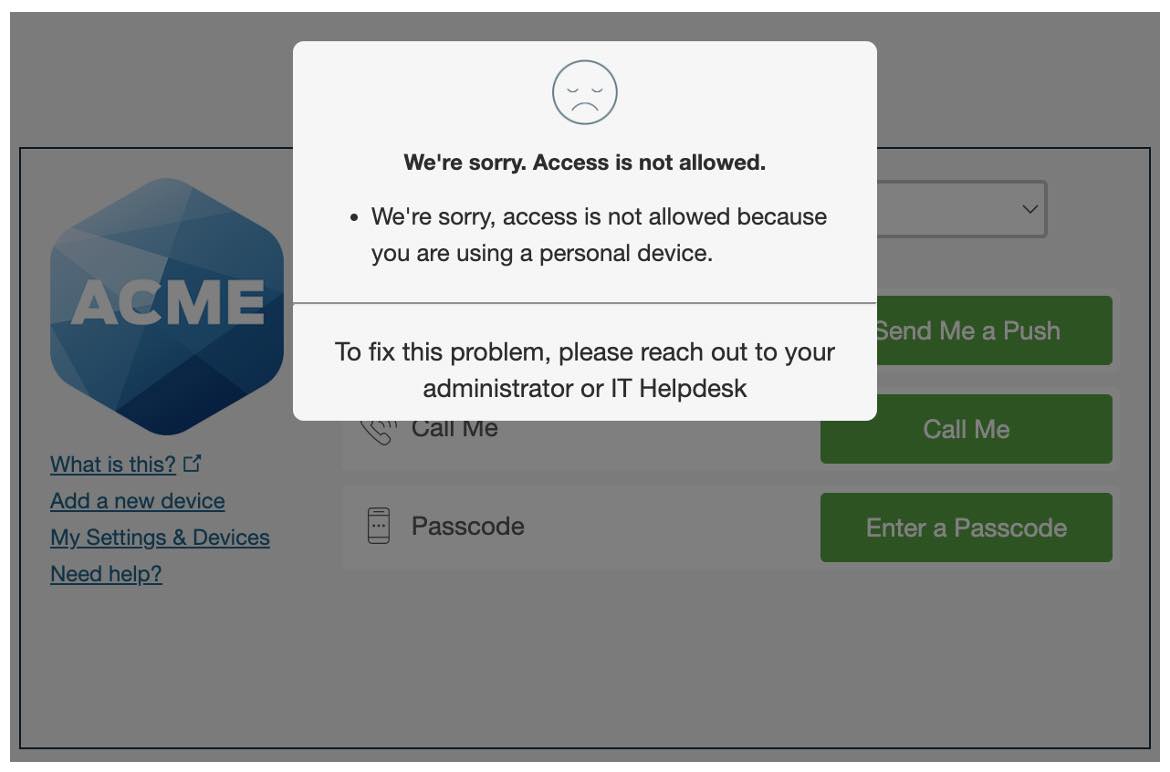
Another option to help secure your students and staff is to roll out Duo Trusted Endpoints. Trusted Endpoints works by registering the user’s endpoint via the Duo Desktop or Duo Mobile applications, then preventing authentication from non-registered devices. In the above scenario, the attacker’s device would not be registered to the trusted user, and the attacker would see the following and be unable to authenticate. For best practices on securely rolling out Duo Trusted Endpoints, see our documentation.
Duo Trust Monitor
If you’d like to be alerted to suspicious activity in your environment and monitor for potentially malicious behavior, consider using Duo Trust Monitor. Trust Monitor uses a set of machine learning models and security heuristics that consider the user’s prior history and typical behavior within an organization. It will then score and rank authentications in the past 24 hours and surface any anomalous activity as a security event for administrators to review. Trust Monitor will also detect and surface risky device registration events.
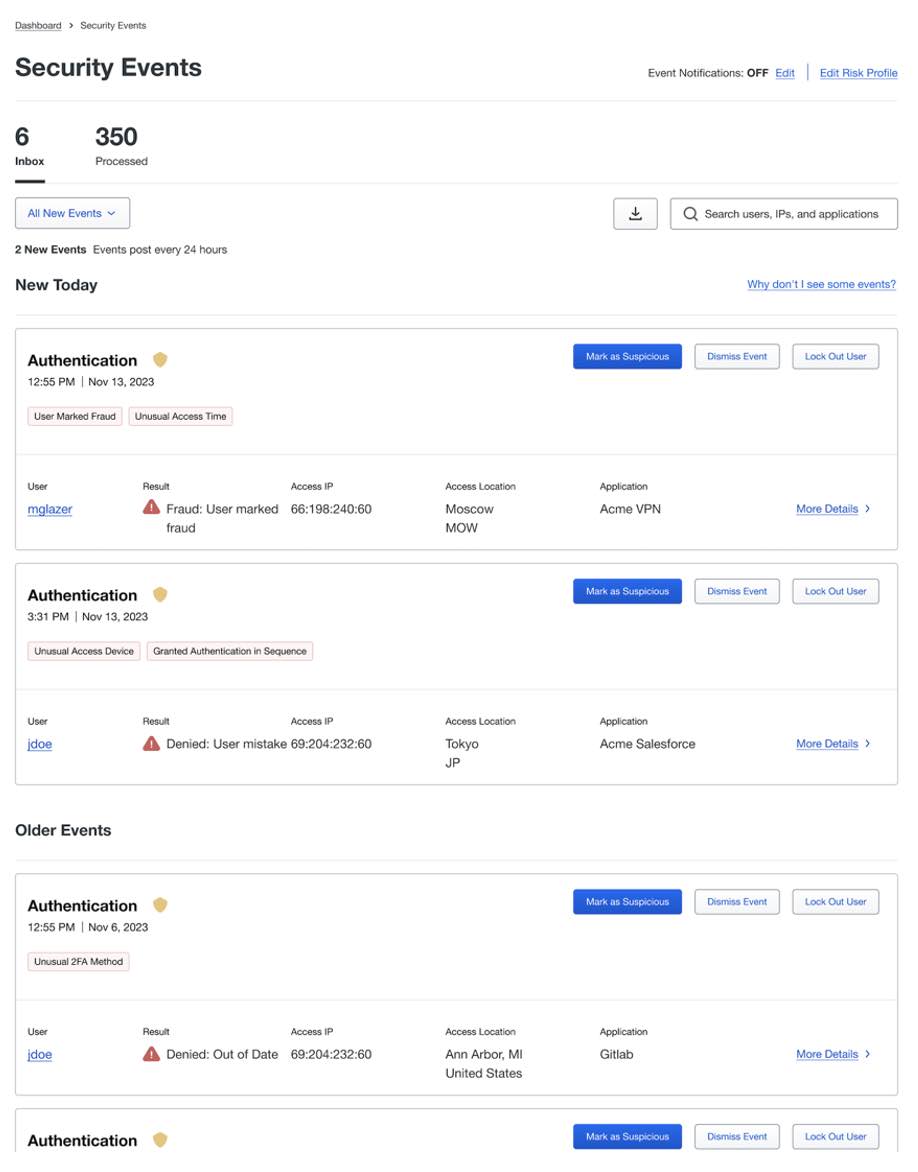
Common signals used in Trust Monitor to identify risky events include the rate of travel between authentications, time of day of the authentication, the operating system of the device attempting access, the authentication factor being used, and the application being accessed. Many of the authentications seen in these attacks would have triggered security events within Trust Monitor due to their unusual locations and operating systems given the users’ respective histories.
Summary
The behavior we have seen indicates that higher education institutions are increasingly being targeted by malicious actors. While Duo MFA is an essential first step in protecting your organization, we hope that the recommendations laid out here will allow you to have more confidence in the safety of your users as you head into the new semester. That way your teachers and students can focus on why you’re at school in the first place, to learn. We will continue to monitor for and alert customers to detected malicious behavior and use these findings to further enhance our offerings.

