Our Mission is to Protect Your Mission.
At Duo, we take security very seriously, and protecting our customers is always first priority. Leave security to the experts and put the focus back on growing your business.

We’re more than a security company.
We’re a Trusted Access company.
People
Mission Control
Your Professional Security Experts
Duo’s full-time security team is experienced in running large-scale systems security. We employ the top mobile, app and network security experts. Our researchers and engineers have worked at Fortune 500 companies, government agencies and financial firms.
Duo is founded by CEO Dug Song and CTO Jon Oberheide, two respected pioneers in the security community with a commitment to driving innovation and growth. Learn more about our team.
Ongoing Security Innovation
Duo is committed to investigating new security concerns. To encourage engagement in the security community, please contact security@duosecurity.com or visit Security Response for any security issues.

Process
Built-in Security
Automatic Updates
Duo follows an agile development cycle, releasing updates in hours and days compared to several months and quarters, typical of other two-factor vendors.
There’s no overhead required to keep our application up to date - we send automatic updates to your users’ devices to ensure they have the latest security patches and features. Consider it the end of maintenance windows for your in-house IT support.
Standardized Security Processes
Duo builds security into each step of our operations, including customer data handling, code release, upgrades, patch management, security policies and more.
We endeavor to meet compliance standards like PCI DSS, ISO 27001, NIST 800 and more. A team of independent third-party auditors regularly audit and review our infrastructure and operations to ensure we’re secure enough to support our customers.

Technology
Security by Design
Secure Authentication
Some two-factor solutions rely on shared secrets to generate token numbers, which, if attackers steal, they can use the information to compromise an organization. Duo’s two-factor solution is designed with security in mind.
We use asymmetric cryptography, keeping only the public key on our servers and storing private keys on your users’ devices in a tamper-proof secure element. Duo never stores your passwords - meaning your logins stay safe.
Designed for People
We know the most effective security solution is one your users actually use. Our solution only requires your users to carry one device - their smartphone, with the Duo Mobile app installed on it. Logging in via push notification is fast and easy.
We strongly recommend using Duo Push as your second factor, a more secure method than SMS passcodes that can protect against man-in-the-middle (MITM) attacks.
High-Availability Architecture
Duo has maintained uptime of greater than 99.99% for more than four years, with a hard service level guarantee backed by SLA. Duo’s servers are hosted across independent PCI DSS, ISO 27001-certified, and SSAE 16-audited service providers with strong physical security.
We provide a high-availability service split across multiple geographic regions, providers and power grids for seamless failover, and our multiple offsite backups of customer data are encrypted.

Data Centers & Hosting
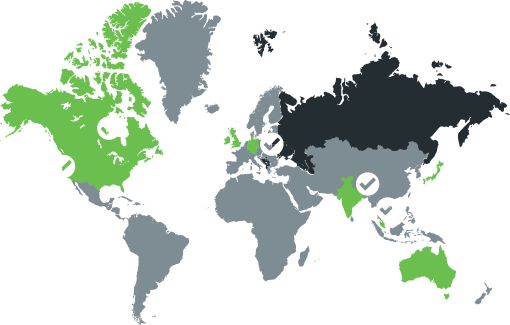
Duo is headquartered in the United States and operates internationally. Our data centers are located in 9 countries: the United States, Canada, Ireland, the UK, Australia, Germany, India, Singapore and Japan.
Technical Specifications
Duo’s data centers are ISO27001 and SOC2 compliant and maintain 99.999% target service availability goal.
All functionality from Duo’s zero trust platform — including multi-factor authentication (MFA), single sign-on (SSO), VPN-less remote access, device trust and adaptive risk-based policies — are available through these data centers.
Why Local Data Centers Matter
Compliance and Confidence
Keeping data local helps you align with national data compliance regulations, while giving users confidence that their data is in good hands.
Reliability and Uptime
Proximity to your data center increases connection stability, making it easier to optimize your security infrastructure and your application environments.
Cost Savings
Duo’s data center manager is responsible for maintaining high availability while reducing power cost, resulting in lower total cost of ownership for our customers.
Where is My Data Center?
Customer Location
Americas
Europe, Middle East, Africa
Asia Pacific
Data Center Location
United States, Canada, Ireland
Ireland, Germany, the UK
Australia, Japan, Singapore, Ireland, the UK, India
-
“Using Duo, we have enabled a culture of multi-factor authentication without it being seen as a burden to the user. The experience is pleasant and the protection is unparalleled.”
— Bryan Smith, Chief Technology Officer, CyberGRX -
“The thing that I personally love about Duo is, the interface is absolutely slick. You just can’t beat the fact that it’s one touch, one button, one press.”
— Paul Pieralde, Principal Product Security Engineer, Eventbrite


