Security Starts With Transparency
Duo’s device trust capabilities provide data on who’s accessing which company applications, and under what conditions — without requiring any agents on your users’ devices.
Verify Trustworthiness of Every Device
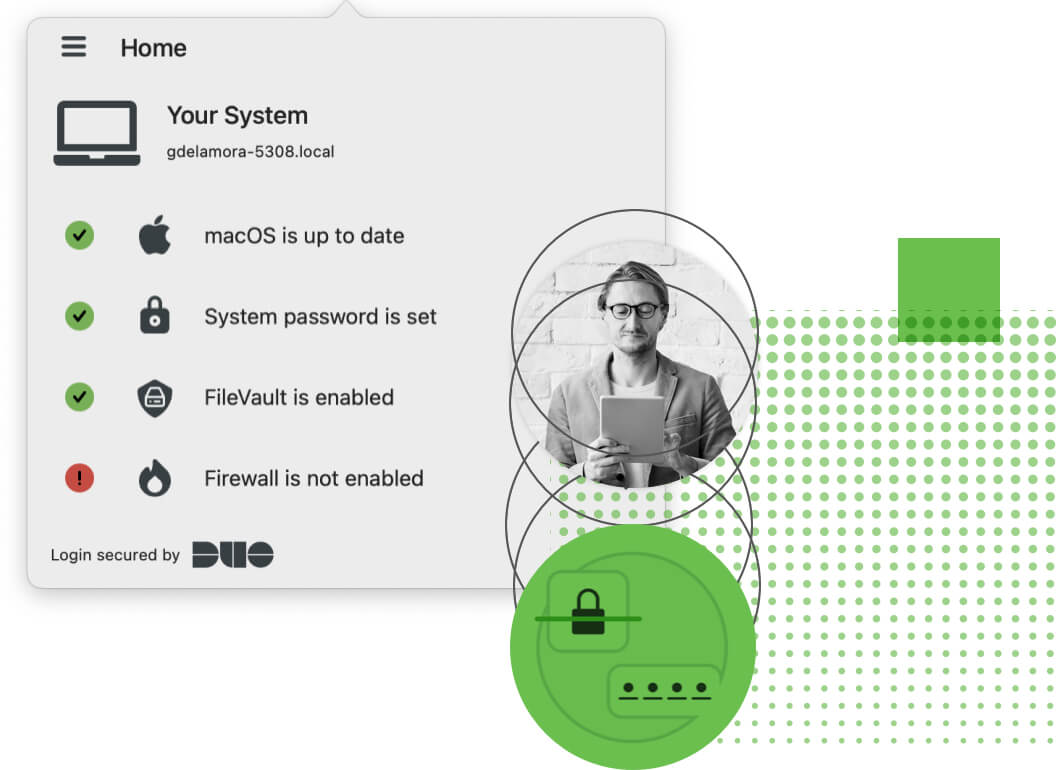
Duo's device trust features give you full visibility into the attributes and behaviors of the devices that access your applications.
Duo’s Device Insight inventories every user endpoint and provides data on operating system, platform, browser and plugin versions, including passcode, screen lock, full disk encryption and rooted/jailbroken status. Easily search, filter and export a list of devices by OS, browser and plugin, and refine searches to find out who’s susceptible to the latest iOS or Android vulnerability.
Duo Trust Monitor takes trust a step further by continuously analyzing authentication data, so that you can spot anomalous logins due to changes in device health, security policies, and user behavior.
Identify Risky Devices and Behavior
Even a trusted user may be using a device with out-of-date software, leaving them susceptible to vulnerabilities. Duo can automatically flag out-of-date devices and continuously monitor logins from any and every endpoint, saving your administrators upkeep time and resources better spent on your core business objectives.
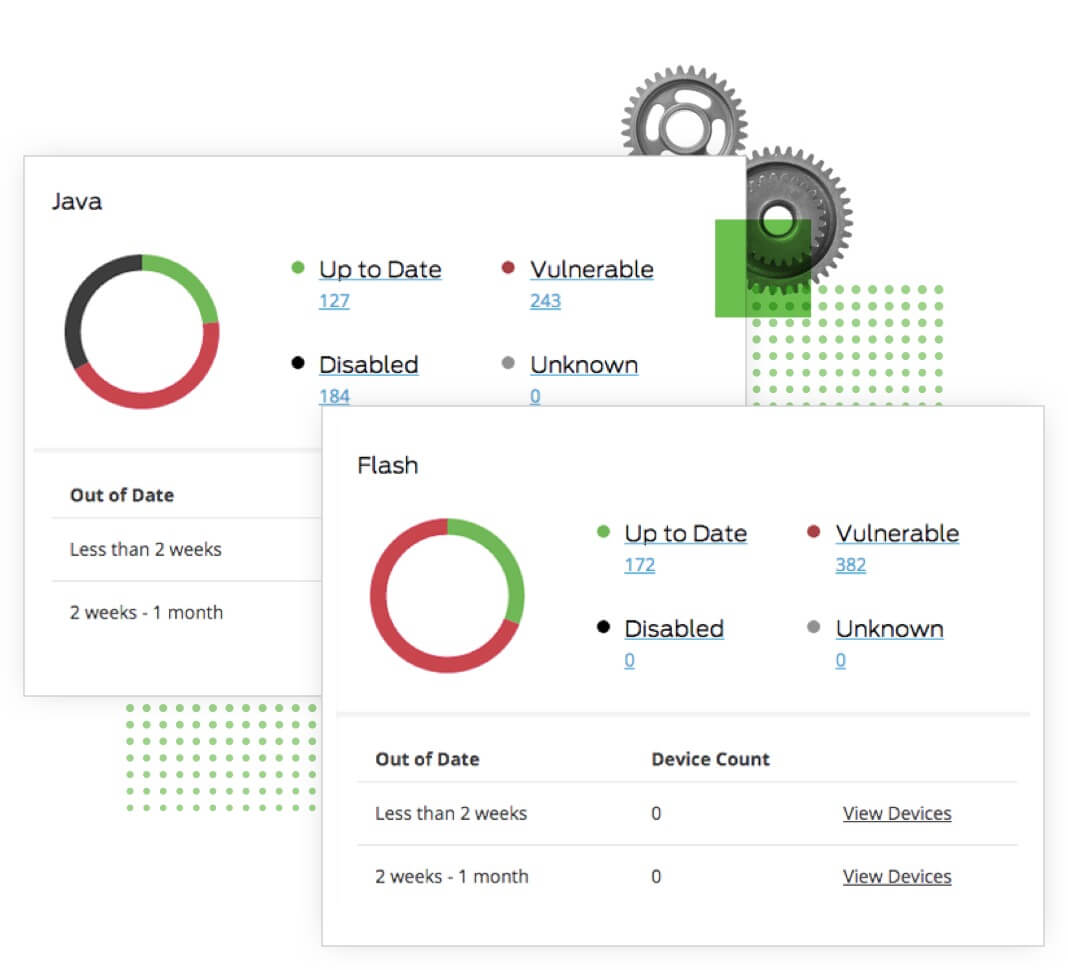
Mitigate Vulnerabilities From At-Risk Software
Adobe Flash and Oracle Java have over 500 known vulnerabilities, putting your users’ devices and the company at risk of a data breach.
Duo gives you insight into software use across your organization, so you can see which users and devices run outdated versions of Flash, Java, and more.
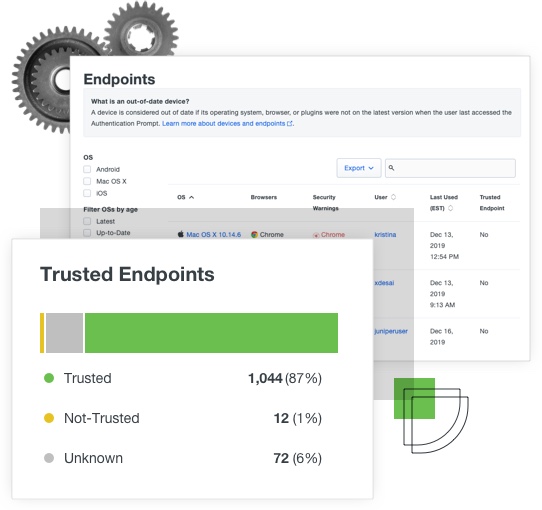
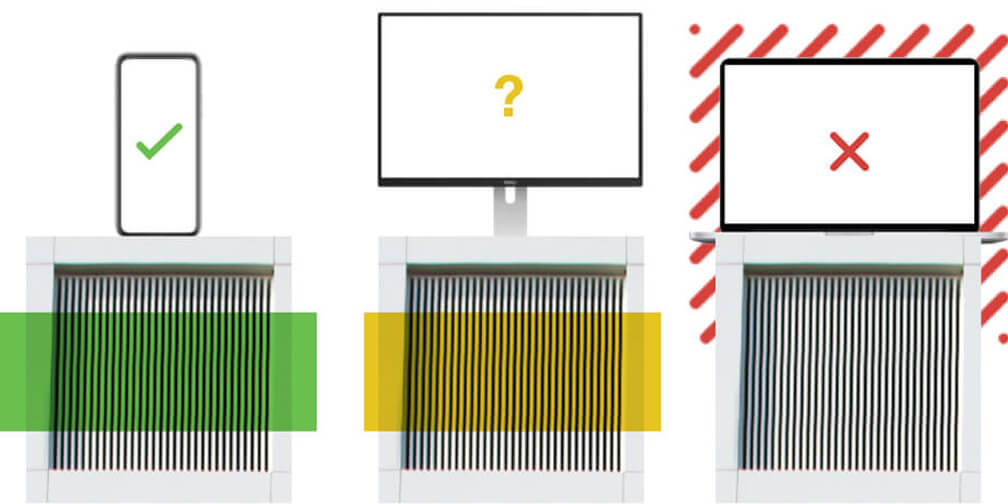
Differentiate Managed and Unmanaged Devices
Secure your BYOD environment by differentiating between company and employee-owned devices that access your applications.
It’s easy to deploy the Duo certificate on your company-issued laptops to mark them as ‘Trusted.’ After that, your Device Insight dashboard will automatically show a breakdown of the trusted (has a Duo certificate) and untrusted (does not have a Duo certificate) endpoints on your network.
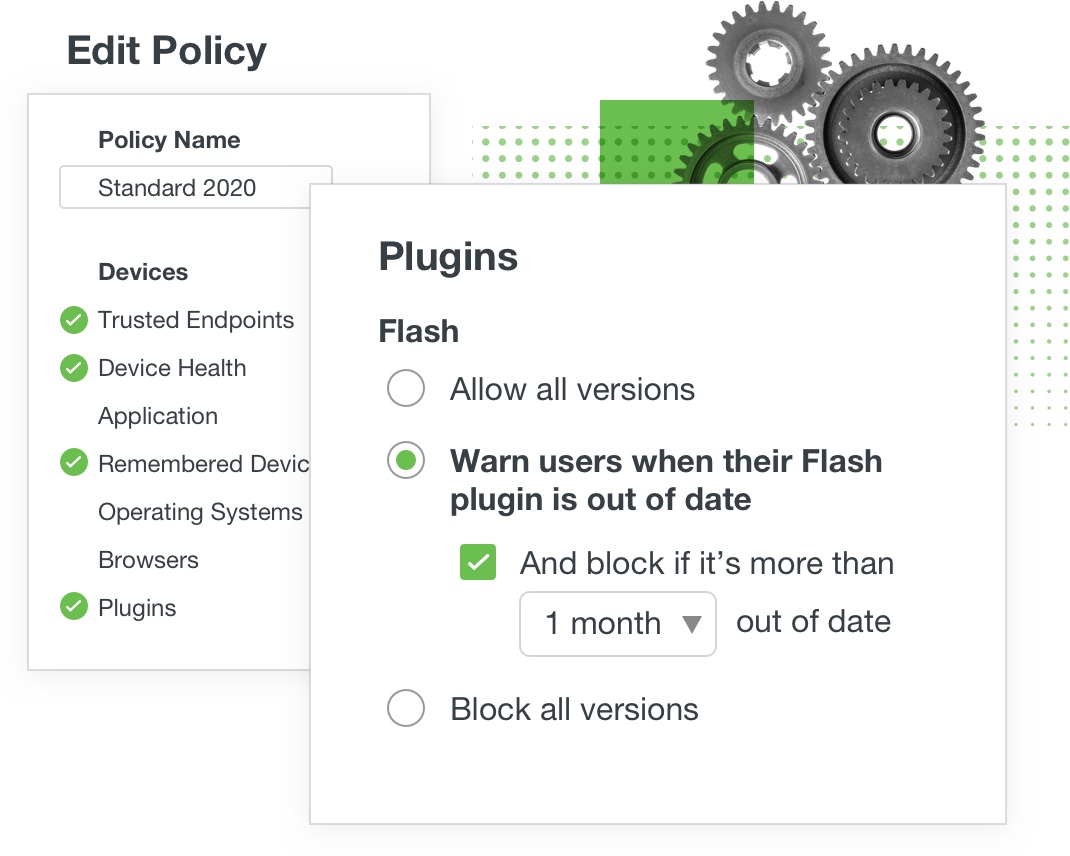
Set Device Access Policies
To prevent the spread of malware and stop risky devices from accessing your applications, create custom access policies and controls based on security health profiles or anomalous access events. Duo’s Endpoint Remediation allows you to block access based on certain device factors. Closing security gaps starts with keeping devices patched and healthy.
For example, you can block any devices running out-of-date Flash or Java until the user updates their device to the latest software version. That way, you can ensure enterprise applications are protected against all known and reported vulnerabilities.