What Are Passkeys?
Can they open your house door? No
Can they open your car door? No
Can they open cloud or on-premises applications from any device without using a password? Yes

Before we can discuss passkeys, we need to lay some groundwork and discuss authentication, Passwordless and WebAuthn.
What is authentication?
Authentication is the process of verifying your online identity. This ensures the right people get access to the right online resources. It also prevents bad actors from doing bad things to your company, including:
Stealing (exfiltrating) important data, like user social security numbers
Installing malware and holding intellectual property (like software code) ransom
Destroying servers or PCs, preventing employees from working
"Over 80% of the breaches categorized under web application attacks can be attributed to stolen credentials, allowing attackers to outright log in rather than break in." - Verizon, 2022 Data Breach Investigation Report (DBIR)
Authentication has been evolving as cybercrime has become more sophisticated. We started with usernames and passwords – something you know. We added multi-factor authentication (MFA) – something you know and something you have or are. We’ve gotten to passwordless (something you have + something you are).
What is passwordless?
Passwordless is the modern authentication method that does not rely on passwords, eliminating the risks that come with weak, lost, or stolen credentials. It is MFA Phishing Resistant. At the foundation of passwordless technology is the FIDO Alliance and the WebAuthn protocol they’ve developed with input from industry giants like Cisco Duo.
Duo Passwordless uses platform authenticators, security keys from access devices, or Duo Push to secure application access without passwords, reducing the risk surface and administrative burden associated with passwords while improving the user experience.
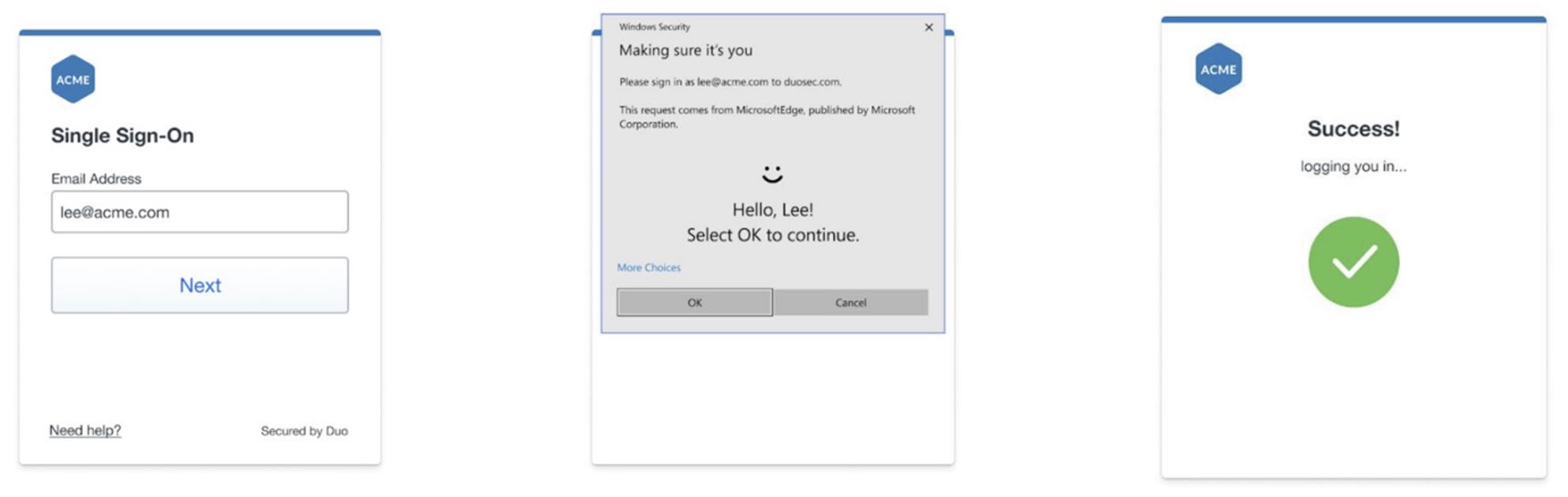
Explore the Administrator's Guide to Passwordless to learn more technical details about it.
"It was exactly what I was looking for, which was a simple and elegant way to use YubiKeys or Windows Hello or Touch ID to replace the password. It simultaneously simplifies a user's life and takes the risky password off the table." - Jason Watts, CISO Inductive Automation

According to the 2022 Duo Trusted Access report:
"...the adoption of passwordless authentication continues to rise. The number of authentications using Duo increased 41%." - Duo, The 2022 Duo Trusted Access Report
What is WebAuthn?
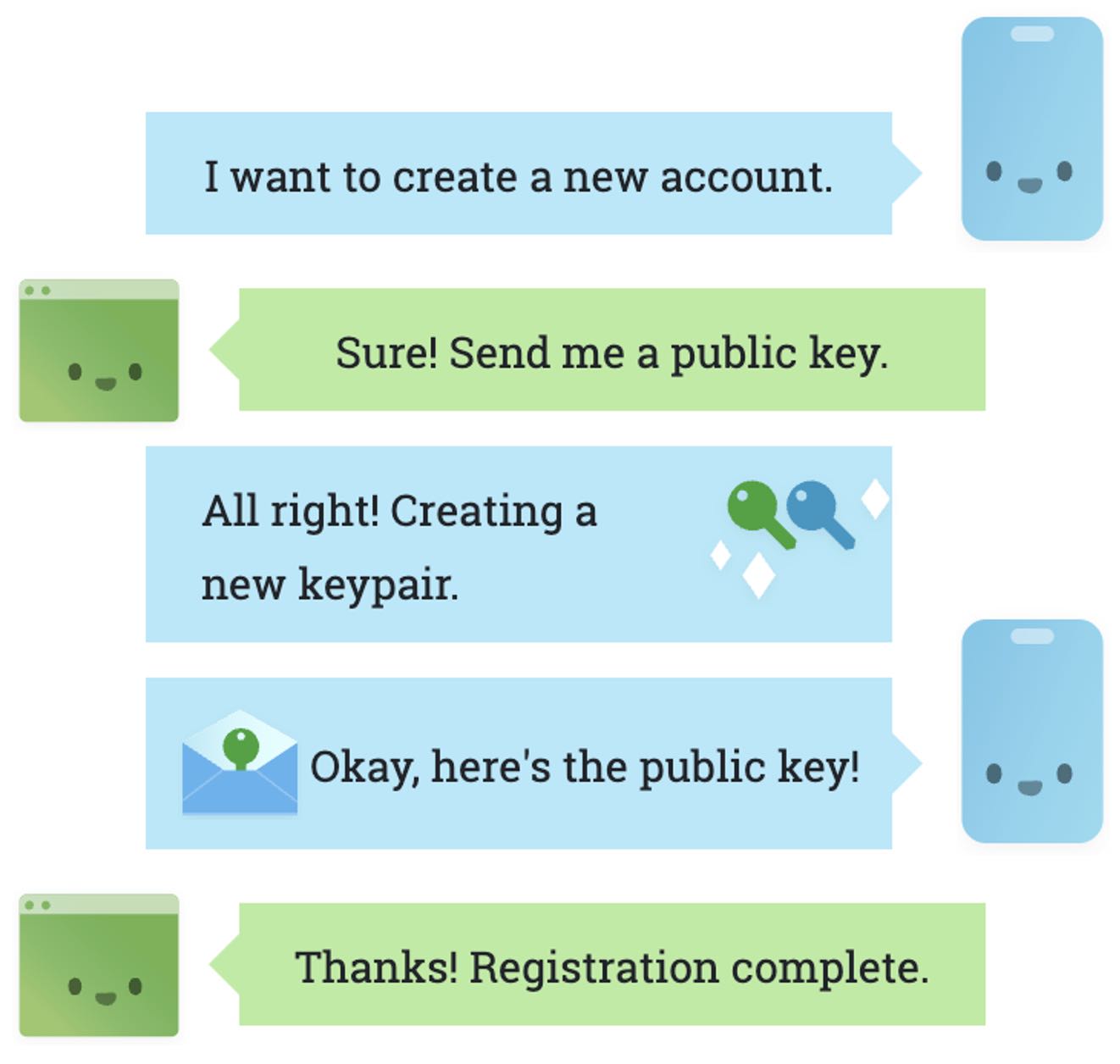
Web Authentication API (also known as WebAuthn) is a protocol and API which allows websites to register and authenticate users with public key cryptography instead of a password. It also allows them to integrate with strong biometric authenticators like Windows Hello or Apple’s Touch ID.
Instead of a password, a private-public keypair is created for a website. The private key is stored securely on the user’s device; a public key and randomly generated credential ID is sent to the server for storage. The server can then use that public key to prove the user’s identity.
The public key is not secret, because it can only be used with the corresponding private key. Therefore, the public key does not need to be stored securely on websites, like with shared secrets. The private key may be stored securely on user devices with encryption technology like Trusted Platform Module (TPM) technology which uses secure tamper-resistant hardware.
According to Gartner®:
"Digital identity hinges on authentication that can provide credence in an identity claim (sufficient to bring account takeover risks within an organization’s risk tolerance), ideally without adding unnecessary friction to the user journey. FIDO authentication protocols, particularly FIDO2, promise phishing-resistant passwordless authentication as a robust alternative to widely used multifactor authentication (MFA) methods, and with better user experience (UX).” - Gartner®, Hype Cycle for Digital Identity™, 2022
What are passkeys?
Passkeys are still “just” WebAuthn credentials. However, passkeys enhance the benefits of WebAuthn-based authentication by offering users the ability to recover from device loss without having to re-register their new device. Passkey “providers” achieve this by securely synchronizing passkey private keys between devices.
Passkey benefits include:
Phishing-resistance and lowered breach impact and cost
Reduced helpdesk load related to forgotten passwords
A more flexible and streamlined authentication flow for users
Increased user satisfaction from an overall better authentication experience
Greater accessibility for users with disabilities through the use of biometrics
A standards-based way for developers to quickly and securely build authentication features into their applications
10 things to know about passkeys
Passkeys are poised as the unique and final solution to eliminate passwords and the pitfalls that come with them
Passkeys have been supported through Apple keychain from September 2022, when Apple released iOS 16
Google added passkey support for Chrome and Android through Password Manager a few months after Apple
Passkeys are created by users on their device and copied across their Apple, Google, or Microsoft accounts on their phones, tablets or laptops
Cross-platform support for passkeys is a stated goal of Apple, Google, Microsoft and the FIDO Alliance, yet it does not exist today
Passkeys do not yet meet the possession requirement noted within the Strong Customer Authentication (SCA) standard, which is a European regulatory requirement to reduce fraud and make online and contactless offline payments more secure; it is under review by the FIDO2 working group
A passkey is a FIDO credential comprised of a cryptographic public-private key pair that’s generated for each target website; the public key is stored on the website’s server, while the private key is stored securely on the user’s authenticator
To sign in, the target website sends an assertion challenge to the user’s authentication; the user enters a pin or verifies their biometric, and their authenticator then signs the authentication with their private key before sending it back to the website; the website verifies the signed authentication assertion using their copy of the user’s trusted public key, and the user is granted access
Passkeys are accessed using the open FIDO2 WebAuthn API standard, while the cross-device sync of passkeys is managed transparently by the operating system
Passkeys cannot be phished, so they transfer the responsibility of detecting whether a link is valid away from the end user
Current Duo passkey requirements
Use of passkeys as platform authenticators currently requires:
Windows 11 and Chrome 108 or later
macOS 13 and Safari or Chrome 108
iOS 16 or iPadOS 16
Android 10 and later
Duo supports the use of passkeys synchronized across devices within a platform vendor’s ecosystem (for example: iCloud Keychain if the user is using an Apple products or Google Password Manager if the user is using Android).
Passkeys for the Duo Admin Panel
As broad access device support for biometrics continues to grow, SaaS site support for WebAuthn spreads and standards for cross-platform passkey support are defined, passwordless will remain a journey. Throughout that journey, multi-factor authentication (MFA) will remain an important security measure. While the goal is for passkeys to replace passwords altogether, in the Duo Admin Panel, you can use a passkey for MFA to strengthen login security.
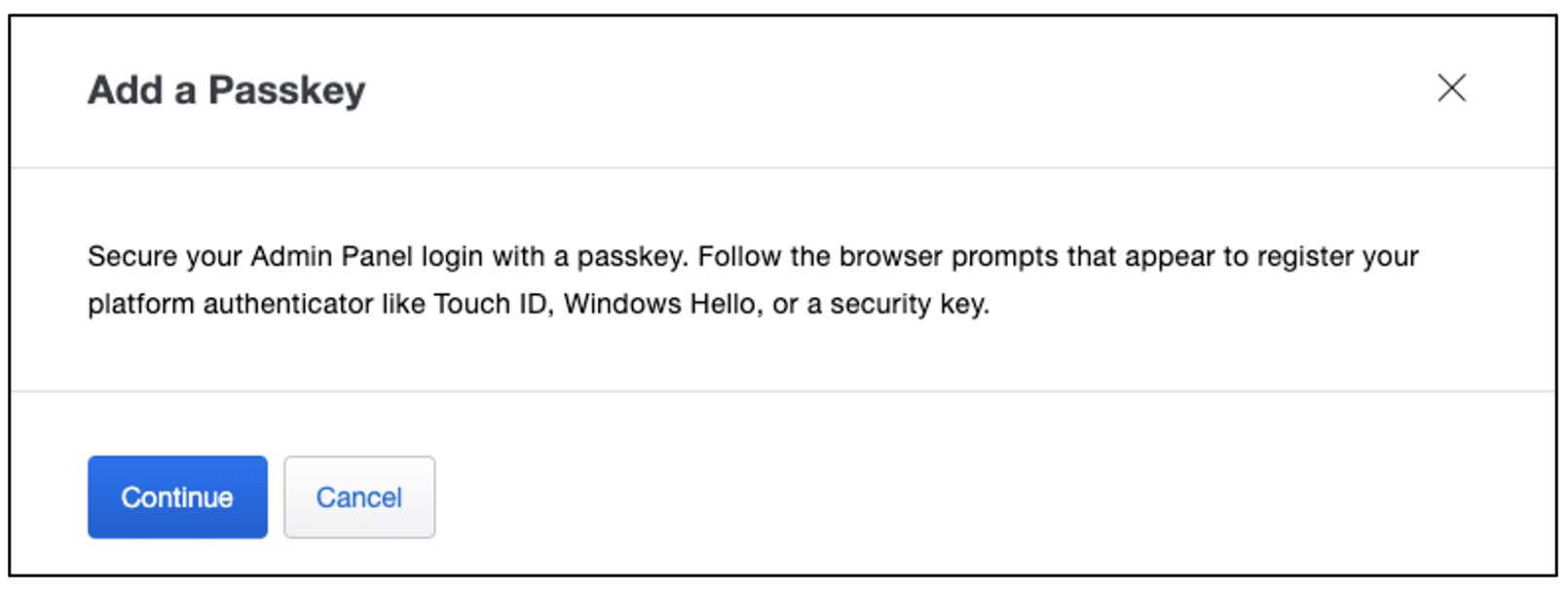
Getting started with passkeys for Duo Admin Panel access
Admins can add passkeys during self-activation or from their profile in the Duo Admin Panel. Owners can also add passkeys for admins through the Administrators page.
Passkeys are enabled by default for Admin Panel access. Owners can change this setting under the Admin Login Settings page in the Administrators section of the Admin Panel.
Gartner® offers the following passkey guidance:
"A 2022 update to WebAuthn to: (1) support multi-device FIDO2 credentials, enabling a user to automatically access their FIDO “passkey” on all their devices without having to separately enroll each device for every service provider (relying party); and (2) enable a user to use their phone as a FIDO2 roaming authenticator to login to an app or website on a nearby device, regardless of the OS and browser that the two devices run. Gartner projects that this update will foster wide availability of fully transportable “phone-as-a-FIDO2-authenticator” apps.” - Gartner®, Hype Cycle for Digital Identity™, 2022
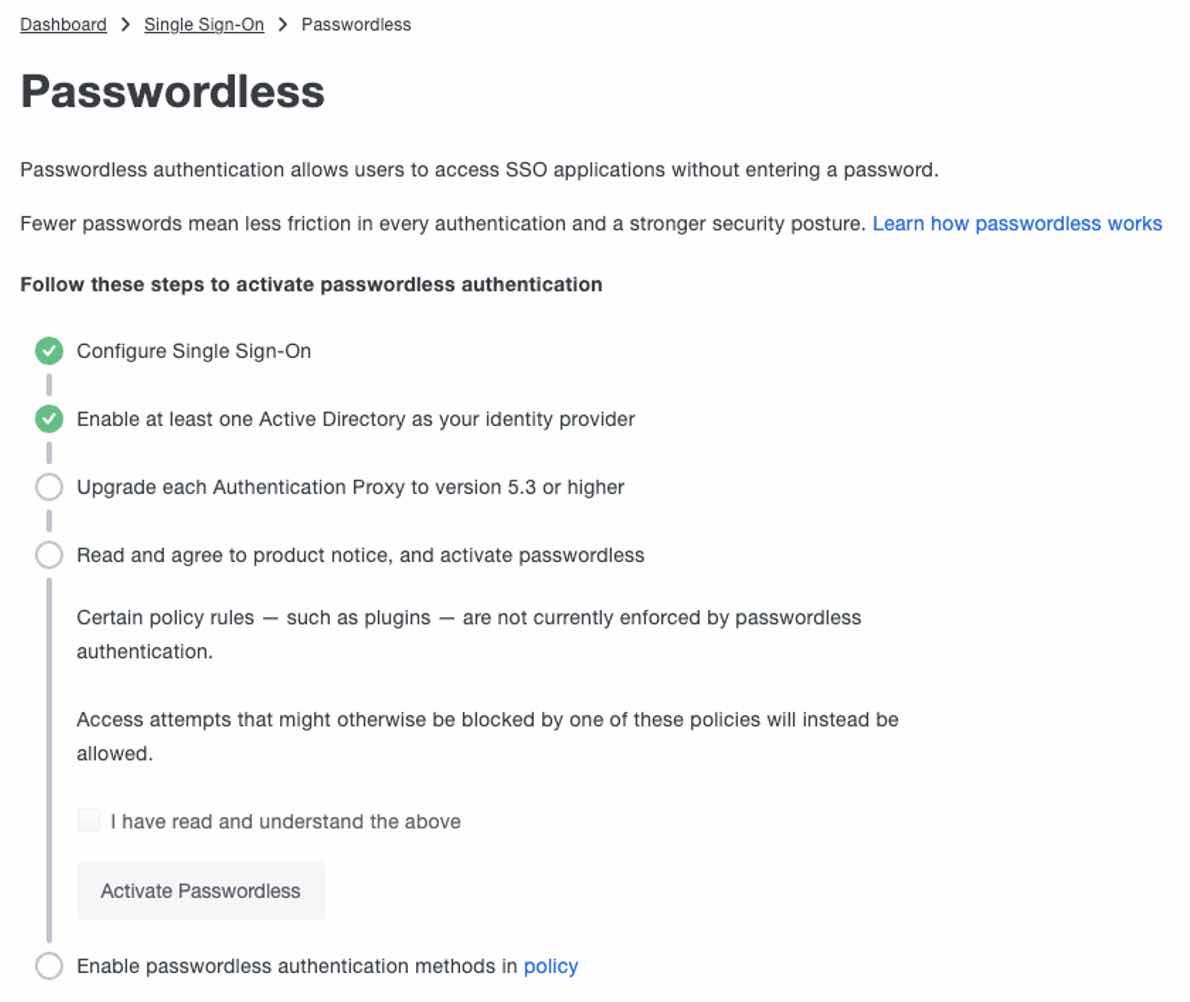
How do you get started with Duo Passwordless?
It all starts with the Duo cloud-hosted console. Enable Duo Passwordless. Pick your Passwordless authentication methods, and apply it to an individual, or pilot group of users. Limit it to users in specific locations or to trusted endpoints which can limit access to verified corporate managed endpoints. And verify that your users' browsers are supported.
Get started with passkeys on your passwordless journey today! They’re available in Duo Essentials, Advantage, and Premier editions. Increase your security posture while increasing your user satisfaction – a win-win solution!

