Protecting Your Universe from Third-Party Threats with Risk-Based Authentication & Verified Push
Captain Marvel, Captain Monica Rambeau and Ms. Marvel are no strangers to teamwork. But when a new villain threatens every place they’ve called home, the Marvels must team up with heroes they know they can trust: Each other.
Whether dealing with contractors, service providers, or other vendors, third-party access management is essential to business. However, the recent spate of software supply chain attacks has heightened awareness amongst security teams and IT on the risks of third parties and how quickly those risks can turn into incidents.
Risk-Based Authentication (RBA) intelligently leverages more secure forms of authentication—like verified push—to help organizations respond to risk and step-up security measures to frustrate attackers, not trusted users. In today’s blog, we’ll talk about how RBA and more secure methods of authentication can securely enable third-party access.
Before we dive in, this is our last call to tune into our webinar ‘Authenticate Further, Defend Faster with Higher Security from Duo’ to learn more about how MFA, SSO, and RBA can work together to protect your environment and pick up some slick, limited-edition sunglasses to fight cyberthreats in style.*
And don’t forget to check out Marvel Studios’ The Marvels, now in cinemas!
A lot of people need – or want – access to your data
Whether you work out of a state-of-the-art S.A.B.E.R. space station or a spaceship traveling across the galaxy, you’ll likely encounter strong access management controls. After all, not just any third-party should have access to the super technology (and super secrets) that our heroes use to save the cosmos.
But just like Ms. Marvel is quick to team up with Captain Marvel and Captain Monica Rambeau, trusted access needs are never a constant. This is especially true when it comes to granting access to your organization’s sensitive resources. A typical organization averages 10 direct third-party relationships, and 25% of organizations have more than 30. It’s not just the direct suppliers that pose a risk to organizations; it’s those suppliers’ suppliers and the fourth, fifth, sixth degree on down the line. In a recent study, about 98% the first-party organizations had a direct relationship with a third party that has experienced a breach in the last two years.
Obviously, Ms. Marvel could be trusted – she’s an important member of the team. And you want to make sure that your security solution can differentiate between valuable allies and dangerous risks. This makes risk-based authentication a critical security measure for protecting against third-party security access risks and helping to keep important data and systems safe.
How does Risk-Based authentication reduce third-party risk?
Risk-based authentication solves two core challenges for an organization: it allows the end user to gain access quickly and easily, and it ensures that access is secure. Some challenges of a risk-based approach include accurately detecting changes in user context and providing flexible controls to match the potential risk. Luckily, over the years RBA technology has evolved to match the demands of a hybrid and distributed workforce, including third-party users.
For example, a company that uses third-party vendors to access its systems can use RBA to require MFA for all login attempts and escalate the authentication method when a new location is detected. This can help to prevent unauthorized users from gaining access to the company's systems through compromised vendor credentials.
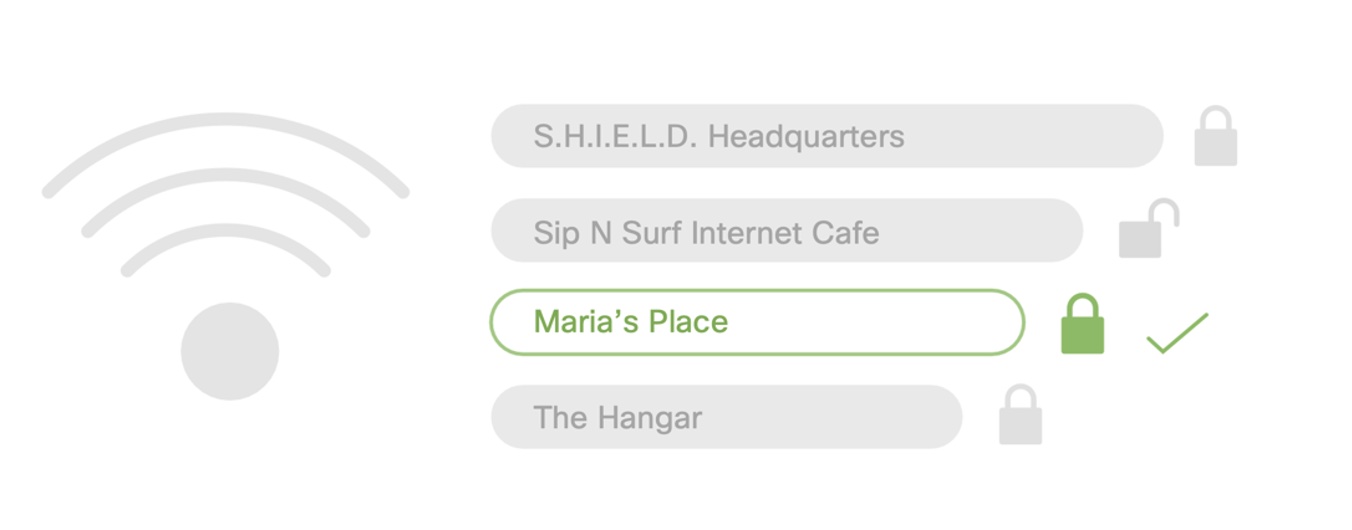
RBA also gives administrators more granular control over how to remediate potential risks. They no longer have to choose between “block” or “allow,” but can instead evaluate where a user falls in the risk spectrum and respond with the equally appropriate friction.
How Duo RBA turns risk signals into smarter security
One simple model for conceptualizing risk-based authentications is by breaking up the login process into three moments: the signal, action, and outcome.
Step 1: Evaluate risk signals
During login, Duo meticulously assesses various signals including user location, browser, and network details from web access requests, along with device attributes and status. Duo’s Wi-Fi Fingerprint technology analyzes changes in location without ever knowing exactly where the user is through anonymized network data, maintaining that individual’s privacy and security.
Step 2: Respond and take action
Duo’s new decision-making engine takes the manual work away from Duo administrators and automatically responds to risk levels. Duo swiftly reacts to these threat signals during login, discerning whether the situation is characterized by high or low trust. This involves contextual risk signals, like an unfamiliar network, or identifying threats using known attack pattern data, such as an unusual surge in push requests.
Step 3: Adjust access requirements
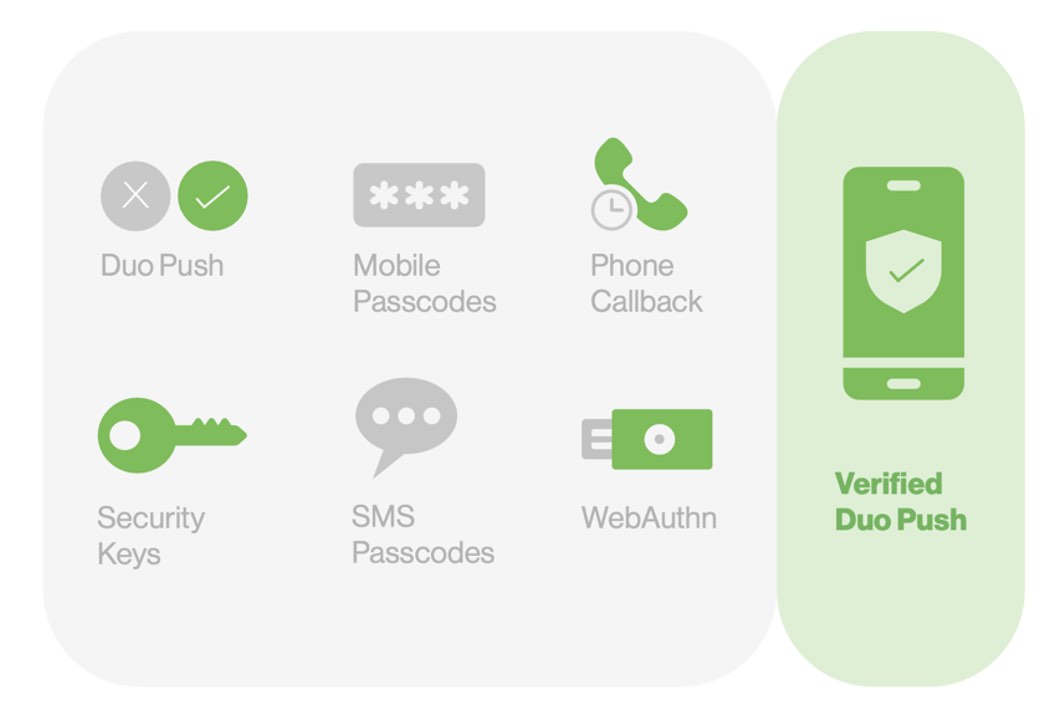
Based on the risk assessment, the user's login experience will entail an appropriate level of security measures. In high-trust situations, the user can seamlessly complete a Duo Mobile Push or forgo an authentication check altogether. However, if the evaluation points towards low trust, the user will be prompted to with a more secure authentication method like Verified Duo Push.
Duo’s Risk-Based Authentication seeks to empower users to gain secure access quickly and safely, without ignoring relevant risk signals. And more importantly, if there are no changes in a trusted user’s environment, Risk-Based Remembered Devices allows users to go about their business with no interruption.
Bumping up security with Verified Duo Push
It can be hard to know who you can and can’t trust when you’re not even sure where you’ll wind up next. When their powers are entangled, Captain Marvel finds herself in a strange bedroom in Jersey City while Kamala Kahn comes face-to-face with a friendly – and terrifying – Flerken.
Instead of having you stop and take stock of allies and enemies every time you find yourself in a new location (which, let’s be honest, is not very effective), duo Verified Push combats known malicious activity like push harassment and push fatigue attacks by asking users to enter a verification code from the access device into the Duo mobile app during the push login process. By using a code, we ensure only verified users can log in and prevent someone absent-mindedly accepting a push they did not request.
Ultimately, the goal of Risk-Based Authentication and Verified Push is to create more roadblocks for potential attackers, without disrupting the lives of trusted users.
Protecting your environment
Captain Marvel isn’t a stranger to working alone to complete missions and protect thousands of planets outside of Earth. But her strengths are only highlighted more when she works with Captain Monica Rambeau and Ms. Marvel to take on the galaxy’s latest threats.
Organizations today rely on their third-party ecosystems to supplement and support critical business functions, and that involves granting users access to sensitive resources. Thus, the goal of a good RBA solution is to take all the burden of evaluating a risky situation away from the end user and put it behind the scenes. With less time spent authenticating and a smoother, uninterrupted workflow, you too can experience fighting threats without one hand tied behind your back.
Learn how Duo can help to protect your environment in our webinar ‘Authenticate Further, Defend Faster with Higher Security from Duo.’ To add some swag to your security experience, attendees will receive exclusive sunglasses that can double as your “super covert” space soldier disguise.*
Don't miss Marvel Studios’ The Marvels, now in cinemas!


