Protecting Against Ransomware 3.0 and Building Resilience
Show me the money!
The number-one reported motive for a cyber breach is financial gain, and ransomware 3.0 is the newest preferred tool to get there.
Tightening cybersecurity has become an increasingly important issue for organisations and individuals around the world. In Australia, the threat of ransomware attacks has been growing, with the Australian economy reportedly losing up to $2.59 billion annually from these incidents.
Twenty-nine per cent of incidents reported to the Office of the Australian Information Commissioner (OAIC) were attributed to ransomware between July and December of 2022, making it the most reported type of security breach of the year. Compromised credentials and phishing attacks, our previous two points of focus in the series, are two of the most common entry paths to ransomware deployment.
In the final instalment of this series, we cover the rise of ransomware 3.0 in Australia and the secure access innovations that make tangible differences in preventing a breach, mitigating the spread, and keeping organisations moving forward.
The Rise of Ransomware 3.0 in Australia
What is Ransomware 3.0?
While ransomware has been around for many years, it has continued to evolve. According to the 2022 Verizon Data Breach Investigations Report, ransomware has increased by 13% over the previous year — a jump greater than the last five years combined. Ransomware 3.0 is the latest iteration of this type of malware, and it differs from its predecessors in several ways, first and foremost in scale.
Unlike earlier versions of ransomware that targeted individual users, Ransomware 3.0 targets large organisations and critical infrastructure. It is also more sophisticated, using advanced encryption algorithms that make it more difficult to decrypt files that have been encrypted by the malware, moving laterally to disrupt cloud applications and taking advantage of inconspicuous crypto-mining schemes.
One innovation driving the proliferation of ransomware is Ransomware-as-a-Service (RaaS) or fully integrated out-of-the-box attack solutions, giving powerful access even with low technical literacy for a small cut of earnings. While Ransomware 2.0 evolved the double-extortion technique of threatening data release in addition to locking systems, Ransomware 3.0 double-downs on monetisation through organised crime and layered extortion methods.
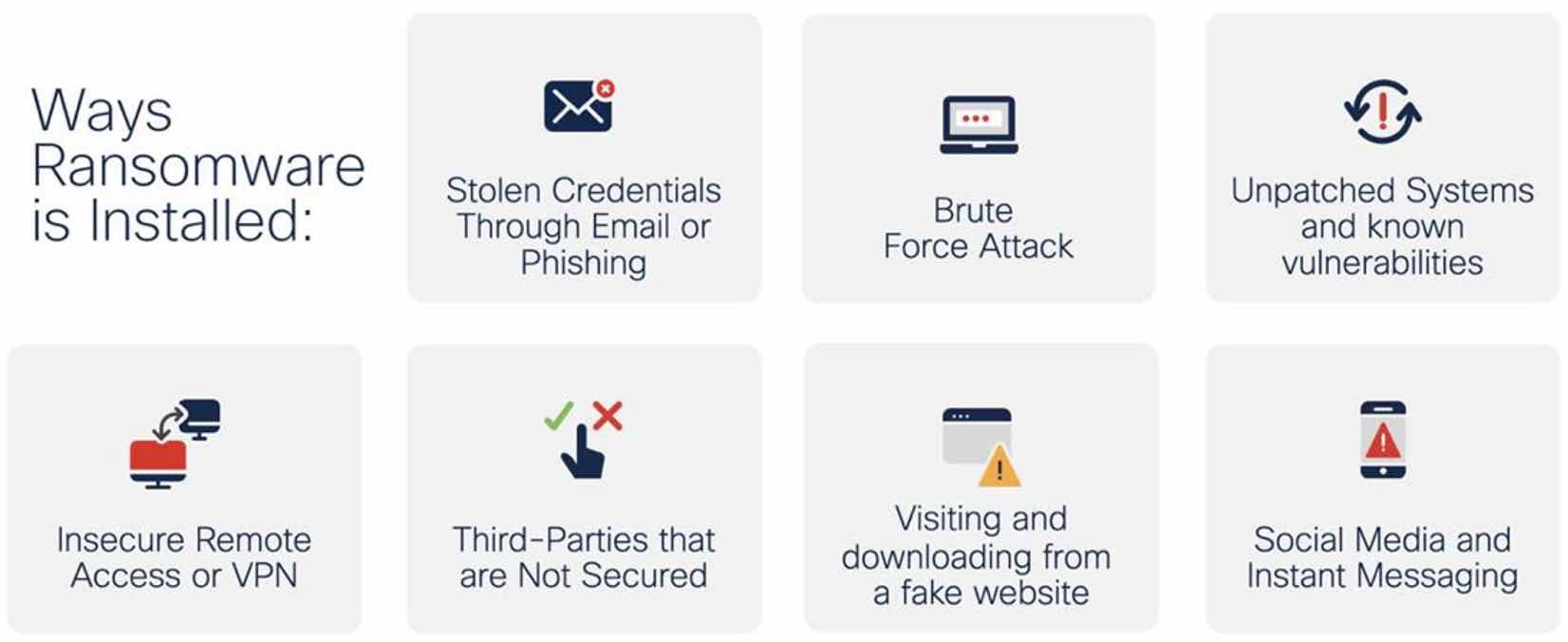
How much does a ransomware attack cost an organisation in Australia?
The cost of ransomware on business is also mounting higher, with Australian organisations paying an average of $250,000 per incident. Cash aside, businesses and individuals must also deal with the costs of lost and compromised data — especially when it comes to personally identifiable information (PII) and personal health information (PHI).
A big target on the healthcare industry
The healthcare industry is particularly vulnerable to malicious attacks such as Ransomware 3.0. The Australian healthcare sector holds a significant amount of PII and PHI, making it an attractive target for cybercriminals and one of the largest reported targets for malicious software by the Australian Cyber Security Centre (ACSC).
Strong cybersecurity in highly digitised healthcare is essential to save lives, where every minute matters. This belief is likewise reflected in compliance and insurance demands, with strict demands for PHI under the Commonwealth Privacy Act and regional legislation (e.g., the Health Records Act in Victoria or the Health Information Privacy Act in New South Wales) and reporting under the critical infrastructure bill.
Rather than temporary patching of security potholes, a strong cybersecurity strategy should evolve with business needs. Ever-increasing regulatory requirements force providers to be ready for current regulations and those that might be enforced shortly. Implementing a model of secure access with solutions like Duo can help mitigate the risk of cyberattacks today and the Ransomware 4.0s of tomorrow.
A Pacific Northwest healthcare provider uses Duo to protect against attacks and enable remote work
A large nonprofit healthcare provider serving over 600,000 residents in the Pacific Northwest is one organisation looking to increase remote work security, improve administrative overhead, and prevent future breach attempts.
In addition to a hospital, the healthcare provider operates a network of more than two dozen primary care, urgent care, and specialty clinics. The administrators wanted complete visibility of all users and devices accessing their Office 365 environment (whether in the hospitals or accessing remotely) and granular access controls through role-based policies for each application.
Multi-factor authentication (MFA) is a critical component of their security program, but the solution that was packaged with the existing enterprise suite did not meet the requirements of the IT security team. After evaluating several market-leading MFA solutions, the team chose Duo because it provided strong multi-factor authentication, complete visibility for workforce access, role-based access controls and the added benefit of ease of use for both administrators and end users.
"When users get phished, bad guys start attempting to use the stolen credentials within 10 minutes. Duo stops these login attempts and provides the details of the login failures so we can take the necessary action. In the last. 90 days, Duo has protected against three instances of account hijacking," said one Security Architect
Duo’s dashboard provides the security administrators with a snapshot of the overall access activity across the organisation, minimising the administrative overhead in user management, monitoring and reporting
“The dashboard gives us a high-level view of our [organisation]. Useful information such as login failures, who logged into which application and when, the number of deployed licenses and inactive users are all available right there. I can then easily drill down to the details of a specific login event with just a few clicks. We did not have this level of information before Duo,” the Security Architect explained.
The healthcare organisation leveraged Duo Care’s expertise to ensure success in deploying and migrating users to Duo with minimal impact on business. Duo’s premium support program, Duo Care, tailored support to the hospital’s unique needs and helped maximise business value. “Duo’s native integration with ADFS gave us the flexibility we needed and made it very easy to deploy in our environment. The rollout was complicated, but we were able to customise the deployment using scripts and we executed it very well,” said the Security Architect.
Migrating to a high-touch solution such as MFA can be daunting and complex as it impacts business productivity. However, using a combination of scripts and user self-enrolment, Duo was rolled out to a group of test users for a month and then to the entire organisation in four days.
Device trust and mitigating Ransomware 3.0 propagation
As with phishing, a layered approach is one of the best tactics against advanced attacks like ransomware.
Duo can help protect organisations from ransomware attacks—including Ransomware 3.0—on three fronts:
Preventing ransomware from getting an initial foothold in an environment
Mitigating or stopping the spread of ransomware if it manages to infiltrate an organisation
Protecting critical assets and parts of the organisation while an attacker still has a presence in the environment and until full remediation is achieved
Strengthening multi-factor authentication is a critical step to protect against ransomware.
Healthcare, alongside education (covered previously when we discussed how dangerous phishing is), is an industry that tends to teeter below the “security poverty line” due to legacy programs and systems; over half of the browsers measured by Duo’s 2022 Trusted Access Report were out-of-date in healthcare.
With Duo Desktop, organisations can perform health and posture checks at the time of authentication to ensure the device meets set security policies before granting access. Without using an agent and keeping user privacy intact, Duo can check whether the OS is up to date, if disk encryption is enabled, if a password is set and more.
Cyber attackers are increasingly targeting gaps in weaker multi-factor authentication implementations. That’s why Duo is bringing protection previously available only in Duo's most advanced edition to every Duo customer. Now included in every tier, Duo’s Trusted Endpoints distinguishes registered or corporate-managed devices from unmanaged BYOD (bring your own device) — with the option to block when an unknown device is attempting to access resources on the network.
Duo's admin panel provides a single-pane-of-glass solution, making it easy to manage policy and monitor security status across all devices. For the aforementioned healthcare provider, Duo helped the team implement role-based access policies per application with ease. While role-based access per application was possible with the incumbent solution, it was cumbersome to implement and manage because each application required a separate instance of the solution.
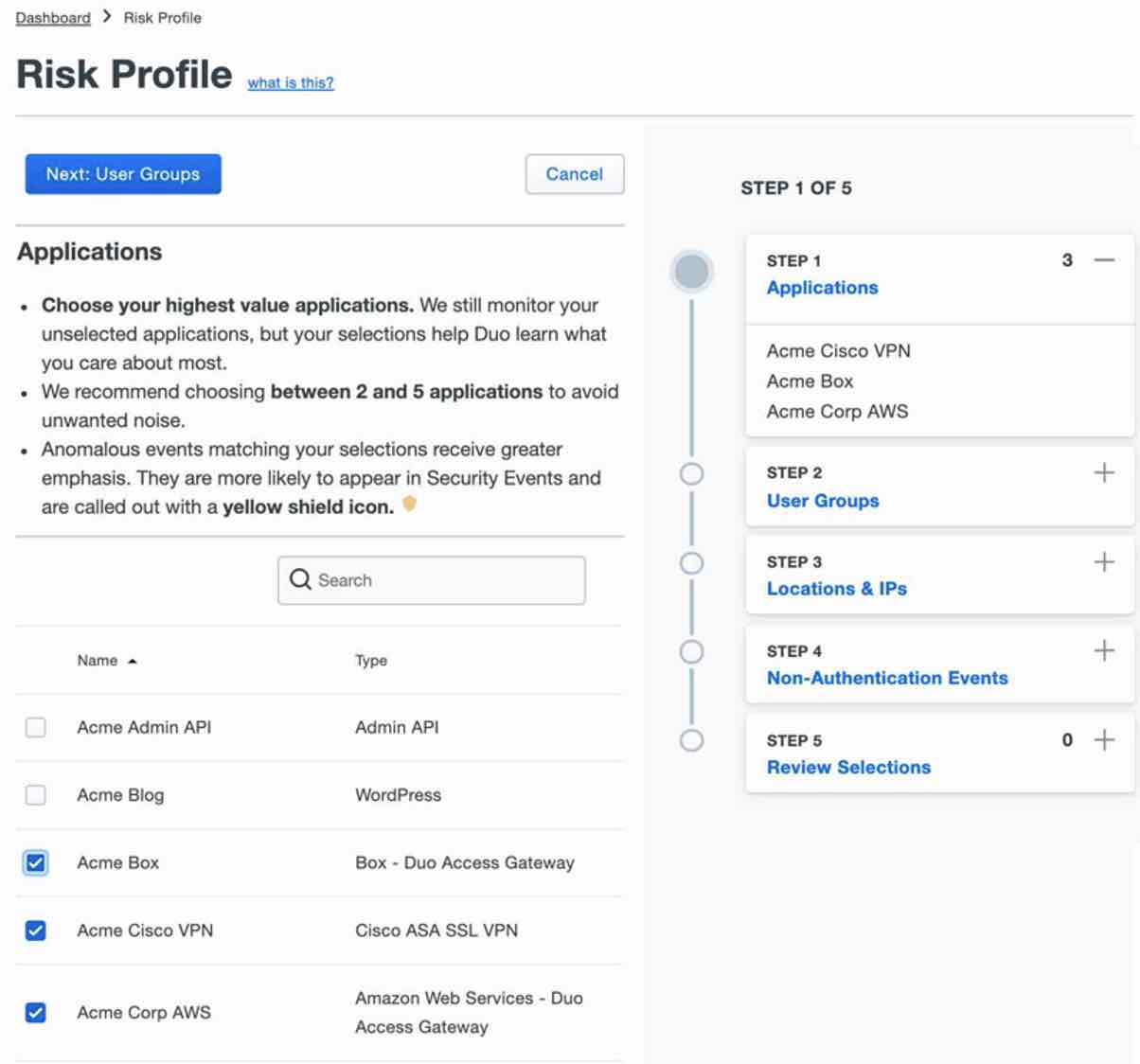
With just a few clicks, administrators can enact new policies or create a Risk Profile in Duo Trust Monitor that prioritises and surfaces security events that match profile elements. Trust Monitor surfaces suspicious logins and alerts administrators when a new enrolment event matches attack patterns seen in the wild.
The bottom line
Yes, Duo and other security solutions reduce the risk and impact of attacks like Ransomware 3.0, but taking a step back reveals the larger goal of strong cybersecurity practices like zero trust in the first place: To keep critical infrastructure online, to launch a new product to market, to move the business forward, or even to keep people healthy and cared for.
Wrapping up: Organisation resiliency
In a few months, cybersecurity professionals will convene at Cisco Live Melbourne to learn and discuss the latest and greatest across security. Last year saw subjects like Secure Access Service Edge, new technological innovations, and the best security practices take centre stage. One theme emerged consistently: resilience and protecting the integrity of business amidst unpredictable changes.
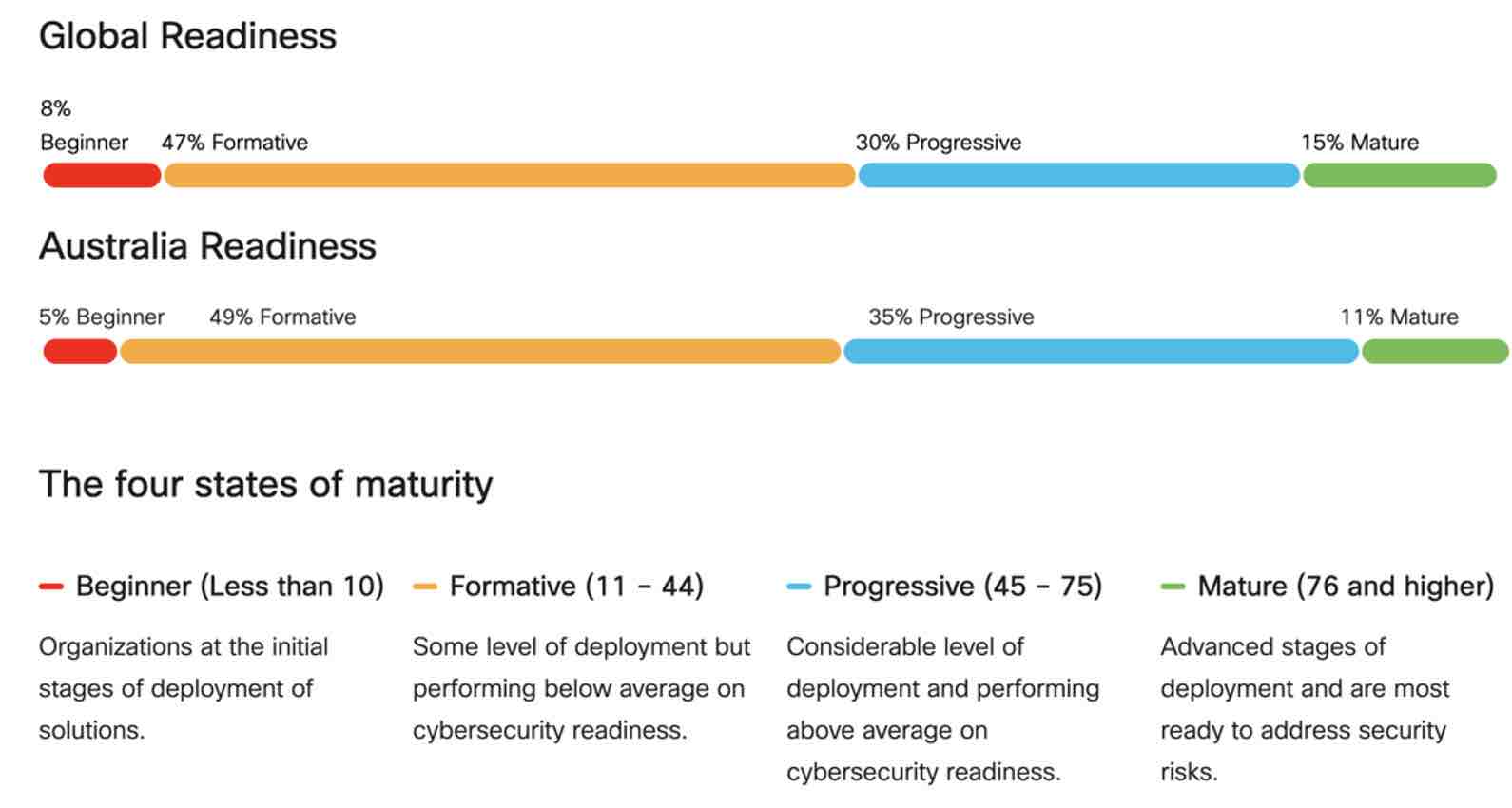
A mere 15% of organisations globally have the 'Mature' level of readiness needed to be resilient against today's modern cybersecurity risks, according to the Cisco first-ever Cybersecurity Readiness Index. Developed against the backdrop of a post-COVID, hybrid world, the report highlights where businesses are doing well and where cybersecurity readiness gaps will widen if global business and security leaders don't act. In Australia, that proportion of mature readiness is 11%.
Every seven minutes, a cybercrime is reported in Australia. The threat of phishing, compromised credentials, and ransomware attacks are growing concerns around the world. Luckily, stronger security solutions exist — ones that don’t impede user productivity and can prove their investment value.
Cybersecurity will continue to be a priority. More than ever, it is essential to embrace the idea of cyber resiliency and continue to evolve security solutions. Today, we can start with securing user access.

