Passwords vs. Passkeys: The State of Passkeys on User Endpoints
These days, users connect to company resources through a variety of endpoints: desktops, laptops, mobile phones, tablets, wearables…the list goes on. And when it comes to managing access for this plethora of devices, password security just isn’t cutting it anymore. That’s where passkeys come in.
In our recent passkey blog series, we’ve been unpacking the difference between new passkey technology and more conventional password security in light of some of the most critical authentication scenarios. Today, we’re taking a closer look at how passkeys compare to passwords from the perspective of user endpoints.
To learn more about the difference between passkeys and passwords – and which solution offers the best value for enterprises – be sure to tune into our webinar, The State of Passkeys in the Enterprise, on September 7th at 9am PST | 12pm EST.
Passkeys on User Endpoints
Passkeys and passwords can both be stored on endpoints. With the former, this is a strength as the private key is stored in a secure enclave and not shared. The latter may be secured in a password manager, yet may also be stored in an open text file or cached in a browser, leaving them vulnerable to endpoint attacks.
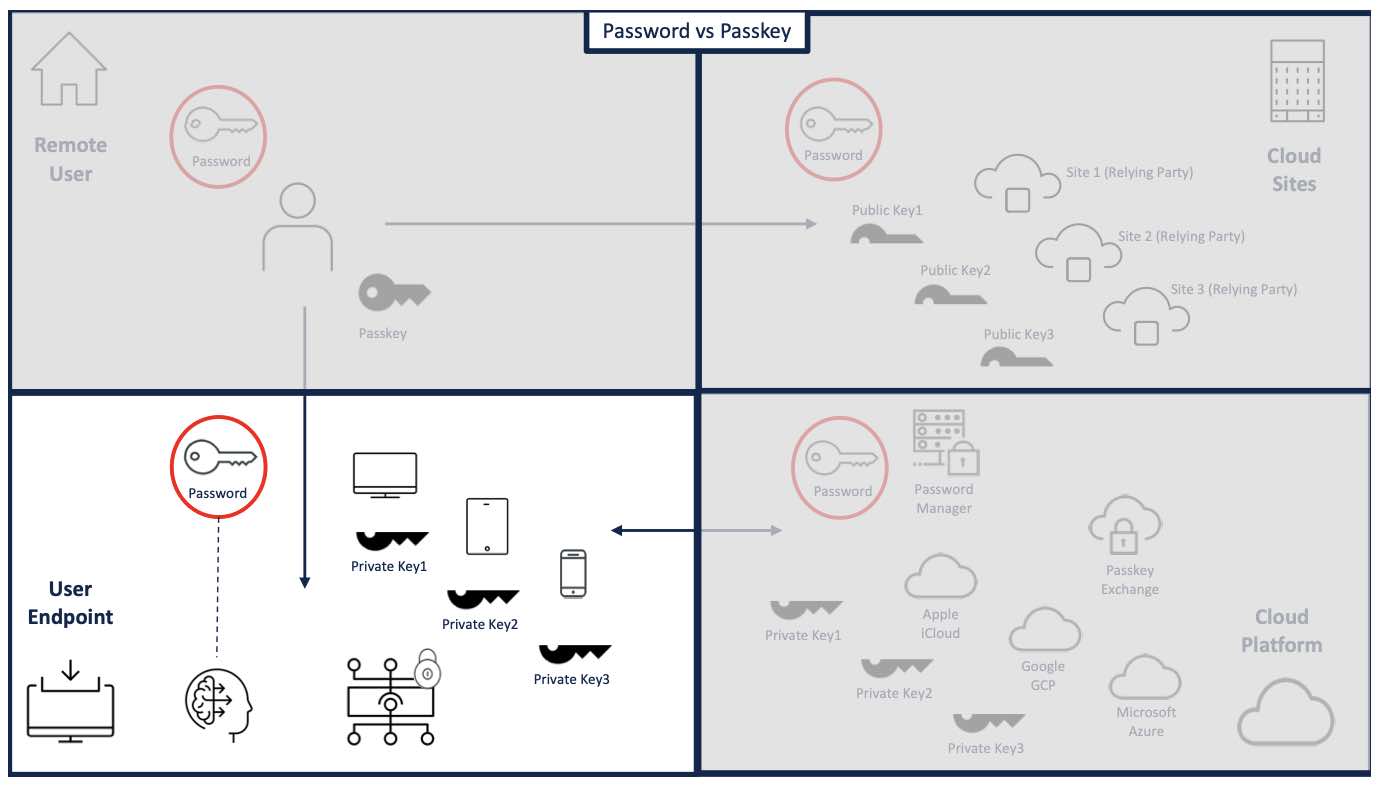
Passkeys are better than passwords
Storage
Passwords can be scraped from a text file or extracted from a browser cache. They’re also vulnerable to malware on the endpoint.
Passkey private keys are typically protected by a hardware secure module, like iOS’ Secure Enclave, and must be present on the device to authenticate.
Multi-Device
Most users employ multiple devices to use their applications. Passwords may be used on all of them, but they must be re-typed, which is difficult on small-form factors. They’re also at risk of theft if they’re left cached on the device.
Passkeys excel at multi-device use. In the Apple or Google ecosystems, they can seamlessly be shared between devices logging into the same iCloud or Google account respectively. They can also be used on other devices through QR code-based “hybrid” authentication.
Passkeys include a new backup eligibility flag, which is determined at the time of registration. When this flag is false, then the passkey should not appear on the other devices. When it’s true, then credentials may be synced to a different device.
Biometrics
Passwords provide no verification of user identity. Once a user’s credentials are known, they may be used by attackers on any system with user accounts, from anywhere.
Passkeys based on the FIDO2 WebAuthn standard can use an authentication device’s local biometric capabilities, like Face ID or Touch ID, to verify the user’s identity and provide multiple factors of authentication in a single interaction.
Passkeys could be better
Shared Devices
Passwords, with or without MFA, are often used by different users to log in and log out of a shared device, like devices in a call center with multiple shifts. Or, they may be used with generic accounts on kiosks, like in retail environments.
Each user account on the same device should have separate passkeys. If multiple users use the same account, though, then a Relying Party would want to use security keys or cross-device authentication exclusively.
While passkeys function on shared devices, users need to be aware they are sharing their identity. Google recommends that, “If you Don’t want the other users to access your account, do not create a passkey on a shared device.”
Local Login
Passwords are often used for local device login, using local accounts stored in secure enclaves maintained by the operating system. Or, they’re used for network login with domain directory accounts over a LAN/WAN or an always-on VPN.
While passkeys were designed for web application support, true passwordless solutions support federated logon to desktops with passwordless SSO and to local and cloud applications alike.
Passkeys with Cisco Duo
Duo’s Trusted Endpoints policy allows you to block or allow devices based on whether they are managed by your organization or registered with Duo.
Duo will check if devices are enrolled in an MDM solution or domain joined. Or, admins can even manually import a list of device identifiers. This prevents users from participating in passkey registration and authentication ceremonies on untrusted devices.
Want to learn more about how passkeys function on user endpoints?
We've got a lot of thoughts on how passkeys stack up against passwords, from the perspective of remote users, cloud sites, cloud platforms and user endpoints. To learn more, check out the rest of the posts in our passkey blog series.
Or, be sure to tune into our webinar to hear from Duo’s experts: Technical Leader Matt Miller, Product Manager Cindy Qu, and Product Marketer Matt Brooks. We’ll talk about current passkey technology, trends in the marketplace, and where passkeys are used within Duo’s passwordless solution. Remember, The State of Passkeys in the Enterprise happens on September 7th at 9am PST | 12pm EST.

