Passkeys vs. Passwords: The State of Passkeys With Remote Users
"Based on FIDO standards, passkeys are a replacement for passwords that provide faster, easier, and more secure sign-ins to websites and apps across a user’s devices. Unlike passwords, passkeys are always strong and phishing resistant. Passkeys simplify account registration for apps and websites, are easy to use, work across most of a user’s devices, and even work on other devices within physical proximity.” - FIDO Alliance
Most people know what passwords are and have experienced first-hand some of the many issues with them. The FIDO Alliance asserts that passkeys are a replacement for passwords. Therefore, we can measure the state, or progress, of passkeys adoption by their readiness to replace passwords. If you are new to passkeys, you can get up to speed with our primer: What Are Passkeys? And be sure to check out our upcoming webinar, The State of Passkeys in the Enterprise, on 9/7 at 9am PST | 12pm EST.
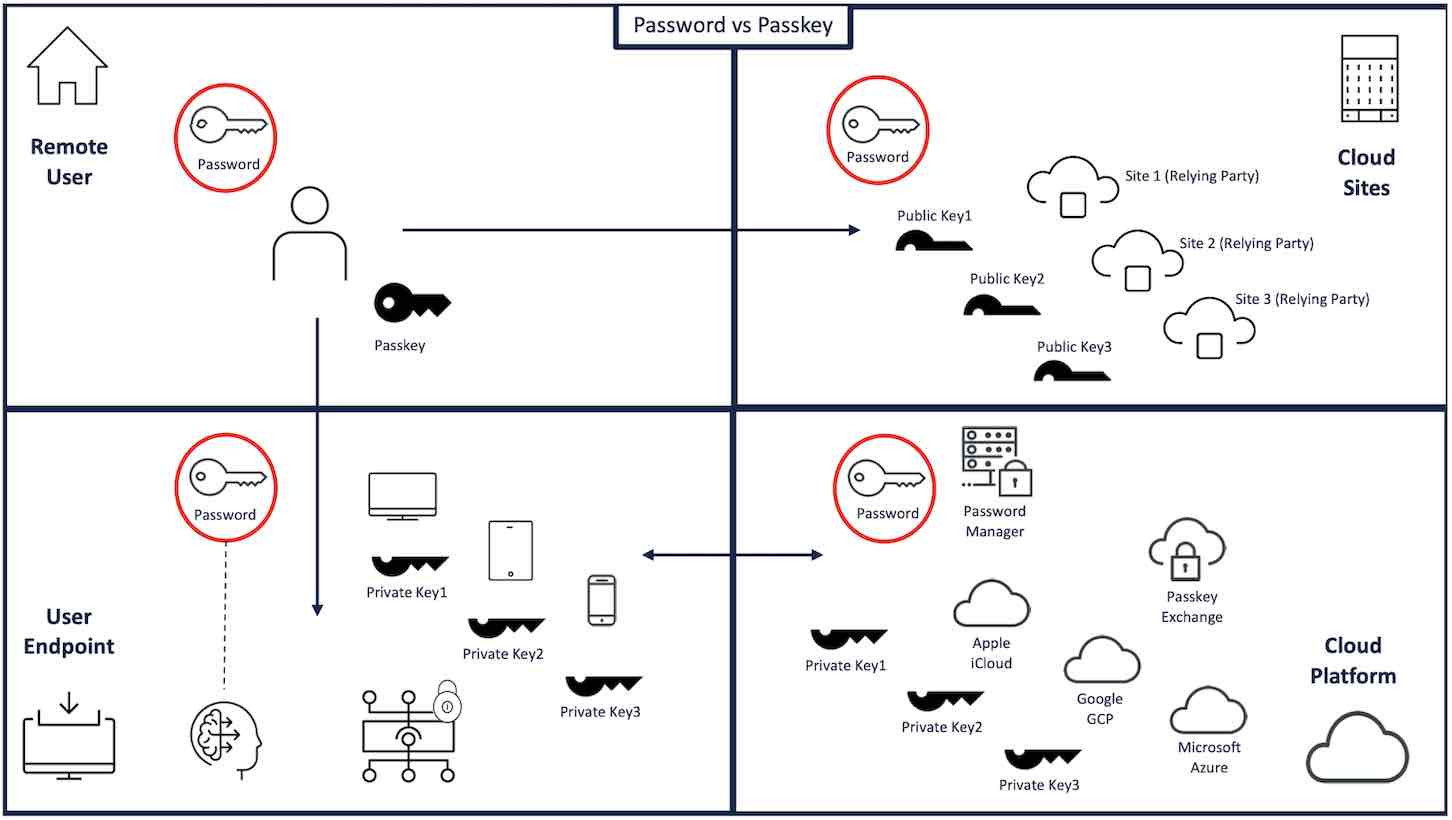
In this blog series, we will look at passwords vs passkeys from four different perspectives in the authentication process:
Remote User – Compare operation and security
User Endpoint – Evaluate endpoint and storage considerations
Cloud Sites – Look at their interaction and use of cloud applications
Cloud Platform – Evaluate how they are handled and managed by key vendors
Today, we're going to focus on how passkeys are better than passwords for remote users. We'll also talk about areas of improvement for passkeys.
Remote Users
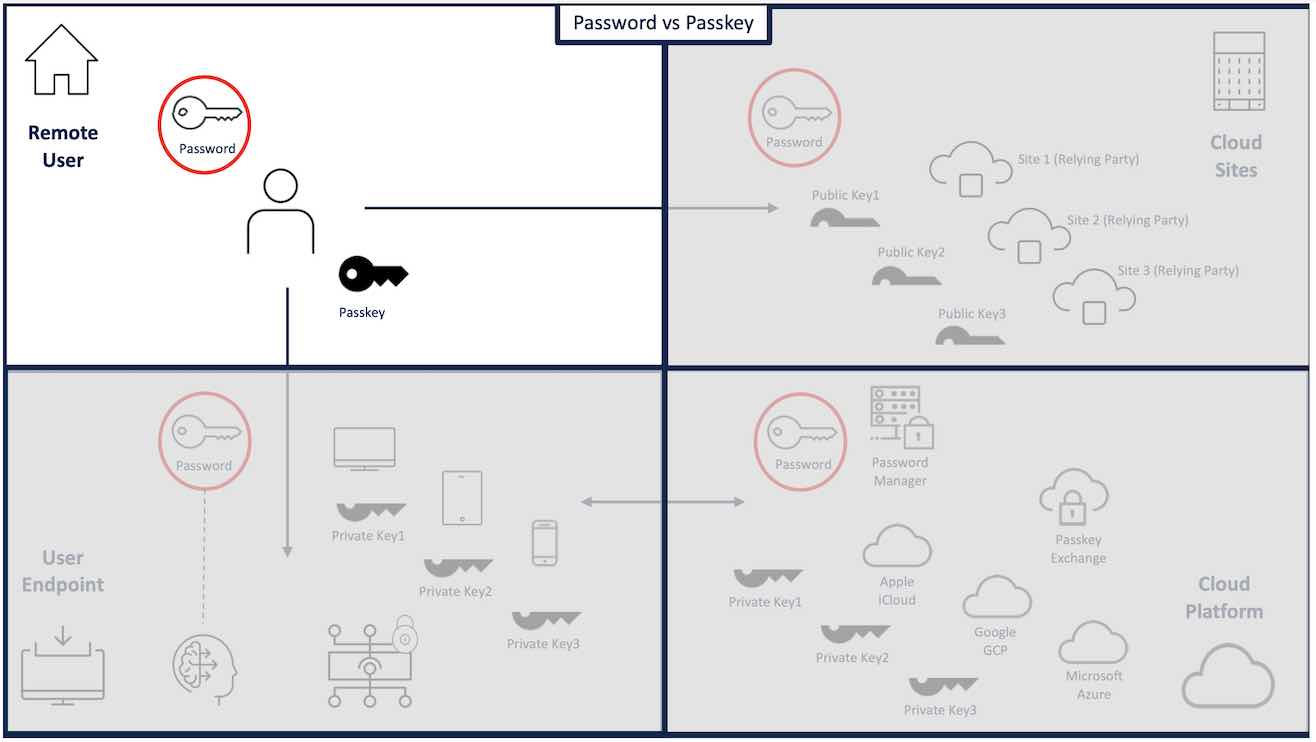
The web authentication process begins when the remote user wants to connect to an application.
Passkeys are better than passwords
Setup
It’s not worth rehashing all the woes of passwords, but to summarize: They’re a challenge for the user to create with complex rules to remember, to change and to manage overall.
Passkeys are created, encrypted and stored by the endpoint for the target application (also known as the relying party). So both initial registration and usage are easier for the user and out of reach to cybercriminals.
Support
Password-related issues are typically a leading consumer of helpdesk and IT support staff time and resources, from providing lockout and reset help to onboarding support.
Passkeys require more support around deployment and enablement. Users need to be trained since they’re a new way of authentication, but typically users can enroll or manage them through a UI-driven workflow by themselves.
Standards
Passwords, also known as Memorized Secrets, were never invented and managed by standards bodies. U.S. government agencies like NIST provide guidelines, but implementation and use vary by vendor and organization.
Passkeys evolved from standards produced by the FIDO Alliance organization, which is a consortium of 250+ vendors that want strong and effective authentication for their users and/or consumers.
Security
Longer passwords with more character options make it harder to decipher or calculate in brute force attacks. But unless users are using a password manager, they often make passwords easy to guess to help remember them.
Passkeys based on Webauthn are proven to be resistant to phishing, credential stuffing, adversary-in-the-middle (AITM), server breaches and may other cyberattacks. Also, they’re designed to work with biometrics, providing high identity verification efficacy.
Multi-factor
Since password-based authentication is so vulnerable, it’s typically paired with other factors. It’s also a requirement to get cyber insurance. Yet many forms of MFA are susceptible to phishing or bypass attacks, and they convolute the user workflow.
Passkeys can be used as a factor to shore up password-based MFA or can be used independently. Google considers them “strong enough that they can stand in for security keys” for use in their Advanced Protection Program.
Private
Passwords by design are stored on target cloud application sites (or by an IDP in the case of Single Sign-On). They are known as “shared secrets” because others have access to them, often including hackers.
Passkeys are designed based on Public-key cryptography.
Efficiency
Passwords require time to type, often followed by a second authentication factor. They’re also difficult to enter on mobile devices without the convenience of a full keyboard, especially when users are entering special characters.
Passkey workflows are designed to be efficient and save time. Also, users do not need to take additional authentication steps that are necessary to protect password-based authentication, like copying and pasting OTP codes from an email.
Passkeys could be better
Enterprise
Although they are highly vulnerable, password-based processes are embedded in enterprises. They’re understood by users and admins alike, and their workflows are well known for onboarding new users.
Although passkeys are a strong authentication method, they use new technology and require workflow optimization by IAM vendors. They also require the development of new processes by enterprises, along with the onboarding that goes with it.
Compliance
Although passwords are inherently risky, they’re less vulnerable with coupled with additional factors. This is supported by the fact that MFA is often required in order for enterprises to obtain cybersecurity insurance.
Although FIDO standards allow for passkeys to be synchronized or to remain device-bound, some regulations need to be addressed. This includes the possession requirement in the European SCA standard for electronic payments.
Virtualization
Passwords may be used on native endpoints and virtual desktops access through native applications or browsers, since they’re entered manually in a web form irrespective of where they’re hosted.
It’s not clear how passkeys and client-to-authenticator protocol (CTAP2) biometrics may be used by virtual desktops. An effective solve for this use case is still being investigated by vendors.
The latest release of Windows 11 does allow for WebAuthn use in virtual machines (VM) using Windows Hello on the machine the user is remoting in from. Remote Desktop will pipe the request and response out of and into the remote machine.
Passkeys with Cisco Duo
Duo is a member of the FIDO Alliance and is helping to evolve passkeys.
Matt Miller is on the FIDO Alliance’s Technical Working Group
Sierre Wolfkostin is on the FIDO Alliance’s User Experience Working Group
Duo remains committed to helping drive adoption of passkey technology. It continues to bet on open-source passkeys for use with FIDO2-enabled web applications, with biometrics verification based on:
Microsoft Windows Hello
MacOS TouchID
Android Pixel fingerprint or facial recognition
Samsung fingerprint or facial recognition
*Duo Push via Duo Mobile secured by biometric, PIN or passcode is available as an alternative when access devices do have biometric readers and subsequently are unable to support FIDO2.
Want to learn more about passkeys?
Tune into our upcoming webinar, The State of Passkeys in the Enterprise, on 9/7 at 9am PST | 12pm EST. Matt Miller, our technical development leader, will join Cindy Qu, our product manager, and me, Matt Brooks with product marketing, to discuss the state of passkeys and where they're used within Duo's passwordless solution.

