Passkeys vs. Passwords: The State of Passkeys on Cloud Sites
Nobody likes passwords. So for many IT teams, the news that tech giants are steadily embracing passkey technology is exciting. After all, passkeys promise both simplicity and security – a tantalizing combination for security teams that are already spread thin. But how effective are passkeys really? And is it realistic to consider passkeys – and the passwordless solutions they support – as a valid alternative for traditional password security?
We’ve been answering these questions in this blog series by unpacking the pros and cons of passkey technology from different authentication perspectives. Today, we’re focusing on how passkeys compare to passwords when it comes to authenticating on cloud sites.
Want to dig in deeper on the password vs. passkey debate? Be sure to check out our upcoming webinar The State of Passkeys in the Enterprise on September 7th at 9am PST | 12pm EST.
Passkeys and Cloud Sites
Cloud sites are where the web applications are hosted. They must support FIDO2 to enable passkey authentication and are also known as the “Relying Party” in the registration and authentication ceremonies.
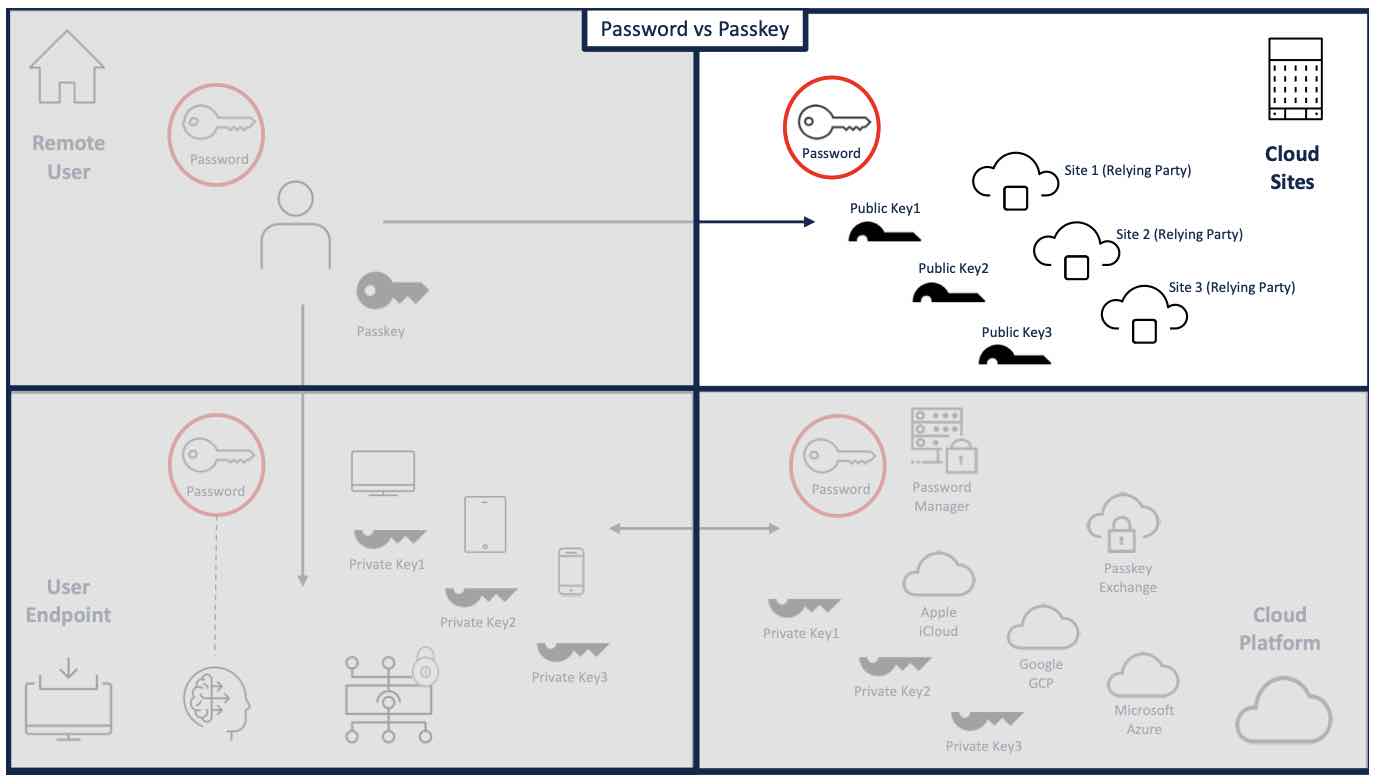
Passkeys are better than passwords
FIDO2
Passwords are shared secrets and do not remain on the local authentication device. Instead, they are shared with target cloud application site(s) and are always at risk along with the integrity of the site’s storage security system.
Passkeys are based on the FIDO2 standard, which means:
No Shared Secrets – There are no shared secrets, and the private key portion of the passkey pair is always kept encrypted locally on the authentication device.
Origin Binding – The site a user is attempting to log into must match the domain, or origin, where the passkey was registered. An alternate site cannot be substituted, mitigating the threat of phishing.
Channel Binding – The communication channel from the authenticator to the website must be strongly tied to the browser session attempting to authenticate.
Development
Passwords, and some forms of MFA developed to work around their weaknesses, are based on legacy protocols and workflows. These are a waste of development resources to build and maintain for application authentication.
Future proof development by becoming a Relying Party. CISOs can confidently include support for passkeys in their application modernization plans, supported by their promise of efficiency and security.
Vulnerability
Passwords may be stolen when users are tricked into entering them in phishing websites. Or, if the cloud site that stores them is hacked, they become available to the highest bidder on the dark web.
Passkeys are split. Only the private key, maintained on the user's endpoint, can be used to sign an authentication request. Passkeys are also never stored on the cloud site, and they cannot be phished thanks to FIDO2.
Passkeys could be better
Multi-Domain Support
Many vendors use multiple domain names for their services, with different top-level domain extensions like .com, .net, .biz, etc. A separate set of passkeys are required to authenticate into each site.
Passkeys with Cisco Duo
Duo provides a broad set of security functionality to support passwordless authentication. This includes Duo Device Health, which verifies device posture and protection status prior to providing authenticated user access.
Duo's cloud-based solution supports a zero trust approach to security for hybrid cloud environments, with adaptive authentication that dynamically evaluates risk signals by continuously analyzing user and device context.
Looking for more information on passkeys?
Passkeys are poised to replace passwords over the long haul, it's in the best interest of IT and security teams to learn about the differences to help drive their passwordless journey.
Be sure to tune into our upcoming webinar, The State of Passkeys in the Enterprise, on September 7th at 9am PST | 12pm EST. I’ll join our development technical leader Matt Miller and our product manager Cindy Qu to discuss current passkey technology and trends. Then, we’ll break down how and where passkeys are used within Duo’s passwordless solution.

