Introducing Duo Desktop, Formerly Duo DHA, Redefining Performance and Security
In the rapidly evolving digital landscape, where threats have become more sophisticated, organizations face the critical task of prioritizing cybersecurity measures to safeguard their sensitive data and digital assets. One of the key elements of a robust cybersecurity strategy is the assurance of endpoint trust in devices used to access sensitive information and applications.
For years, Duo has played a pivotal role in ensuring that endpoints meet the specific security standards set by organizations. The Duo Device Health application (DHA) conducts comprehensive security posture checks on endpoints to provide a comprehensive evaluation of a device’s health and security status so that only healthy and known devices get access to protected applications.
Duo's unwavering dedication to security and user experience has resulted in seamless integrations with other vital features within the Duo ecosystem, such as Trusted Endpoints. This integration simplifies and improves our experiences without sacrificing security.
With all that said, the Device Health Application goes beyond conducting health checks. In order to emphasize its enhanced functionalities, like establishing device trust, Duo has made the decision to rebrand it as Duo Desktop, effective November 2023. By embracing the Duo Desktop app, along with our Duo Mobile app, organizations can confidently identify the device, the user and the context of the access request to fortify their cybersecurity posture across desktops and mobile devices.
The health checks you are familiar with
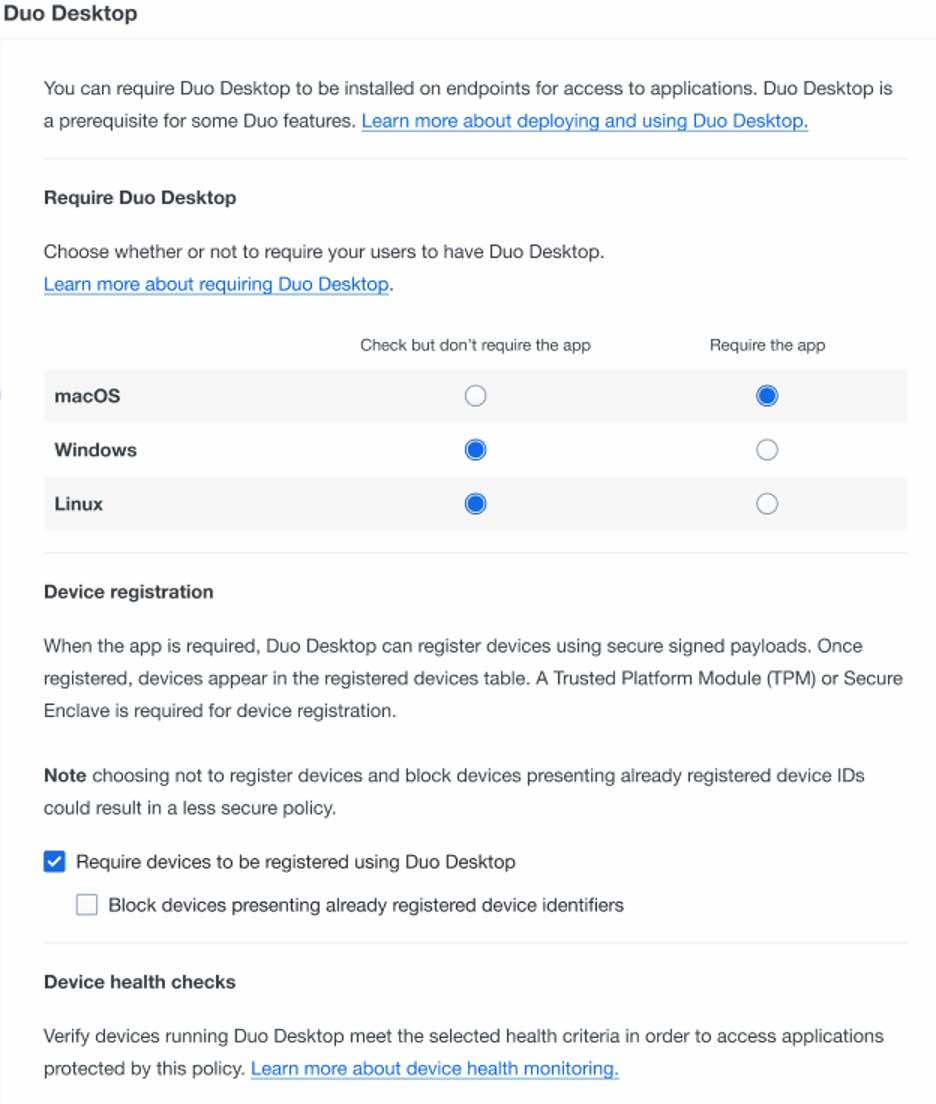
Duo Desktop will continue to exist as a lightweight agent installed on a user’s endpoint. At its core it will offer comprehensive security posture checks which include:
Operating system version and updates
Firewall status
Device encryption status
Presence of system password
Antivirus agent status (Duo Premier edition)
This helps mitigate potential vulnerabilities, such as outdated software, a lack of security agents, and misconfigurations that can be exploited by bad actors to gain unauthorized access to an organization's network. By enforcing compliance, organizations can significantly reduce the risk of these vulnerabilities being exploited.
Expanded platform support
Organizations are constantly striving to safeguard their endpoints, which span across a wide range of operating systems and environments. Understanding the importance of this, Duo Desktop has recently expanded its support beyond Windows and macOS operating systems, to include Linux desktop systems as well.
We also recognize that many organizations operate in a hybrid setup, utilizing both physical and virtual machines. To address this, Duo Desktop is actively working on extending its support to include Windows Server and various virtual desktop environments such as VMware Workstation, AWS Workspaces, and Windows 365 Cloud PC, among others.
By ensuring comprehensive compatibility, Duo Desktop seamlessly integrates with your organization's infrastructure to enhance security across your entire fleet of endpoints. This commitment to compatibility guarantees that Duo Desktop will be available for your unique setup.
Integrations with Trusted Endpoints
In order to ensure a truly comprehensive endpoint security policy, it is not enough for the endpoint to simply meet the security requirements set by your organization. It is crucial that the endpoint is a trusted device that can be granted access to the protected applications. To establish this trust, certain factors need to be verified, such as whether the endpoint is managed by a system management tool and the owner of the endpoint.
Duo Desktop provides a solution that addresses these requirements seamlessly. Through its automatic registration feature, all the necessary information is captured behind the scenes during enrollment. Furthermore, Duo Desktop employs anti-spoof measures that sign all payloads originating from the application to ensure authenticity. Additionally, it establishes keypairs for secure data exchange, which helps prevent malicious actors from impersonating or causing their device to impersonate trusted devices.
Duo Desktop offers a superior experience for determining the trustworthiness of an endpoint compared to traditional methods such as certificate usage.
The future of Duo Desktop
The journey with Duo Desktop is just beginning, and there are numerous exciting developments on the horizon. Duo Desktop will serve as the central hub for many of the innovative and cutting-edge initiatives that Duo is currently addressing.
At Duo, we are constantly striving to stay one step ahead of cyber criminals, anticipating their tactics and finding proactive solutions to counter them. Our ultimate goal is to empower organizations with a comprehensive and user-friendly solution that not only safeguards their digital assets but also provides a seamless and uninterrupted workday for their employees.
Stay tuned for the exciting advancements that lie ahead, as Duo Desktop continues to lead the way in protecting endpoints and more while delivering an unparalleled user experience.
If you’d like to try Duo Desktop for yourself and experience how it verifies endpoint health and trust, sign up for a free 30-day trial.

