Contents
Overview
Duo's Trusted Endpoints feature secures your sensitive applications by ensuring that only known devices can access Duo protected services. When a user authenticates via the Duo Prompt, we'll check for the access device's security posture in Cisco Secure Endpoint.
The Cisco Secure Endpoint solution for Trusted Endpoints is part of the Duo Essentials, Duo Advantage, and Duo Premier plans.
When Duo and Cisco Secure Endpoint have shared visibility into a Windows or macOS endpoint, Duo can block user access to applications protected by Duo from endpoints deemed compromised by Cisco Secure Endpoint. This is accomplished by:
- Deploying one of Duo's Trusted Endpoints management integrations that supports the Cisco Secure Endpoint integration to the endpoint.
- Deploying the Cisco Secure Endpoint Connector application to the endpoint.
- Connecting your Duo service to your Cisco Secure Endpoint service.
These instructions assume you already have Cisco Secure Endpoint already deployed and actively monitoring your Windows and macOS endpoints. For instructions specific to deploying Cisco Secure Endpoint please refer to the Cisco Secure Endpoint support documentation.
Prerequisites
- Access to the Cisco Secure Endpoint administrator dashboard.
- A supported version of the Cisco Secure Endpoint connector installed on your endpoints: at least version 7.1.1 on Windows or version 1.12.1 for macOS.
- Access to the Duo Admin Panel as an administrator with the Owner, Administrator, or Application Manager administrative roles.
- A previously configured and enabled device management integration that supports the Cisco Secure Endpoint integration:
- Windows: AD DS, LANDesk, Windows Enterprise Asset Management Tool
- If your device management integration uses Duo Desktop to check the endpoint status then deploy Duo Desktop to the endpoints enrolled in Cisco Secure Endpoint.
- macOS: Jamf, Mac OS X Enterprise Asset Management Tool, Manual Enrollment
- Windows: AD DS, LANDesk, Windows Enterprise Asset Management Tool
Create the Cisco Secure Endpoint Integration
- Log in to the Duo Admin Panel and navigate to Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, click the Endpoint Detection & Response Systems tab.
- Locate Cisco Secure Endpoint in the listed integrations and click the Add this integration link to the right.
Keep the Duo Admin Panel open in your browser. You'll need to refer to the Cisco Secure Endpoint page to complete the configuration steps.
Configure the Cisco Secure Endpoint Integration
-
Login to the Cisco Secure Endpoint management console.
-
Click the Accounts menu item at the top of the page and go to API Credentials.
-
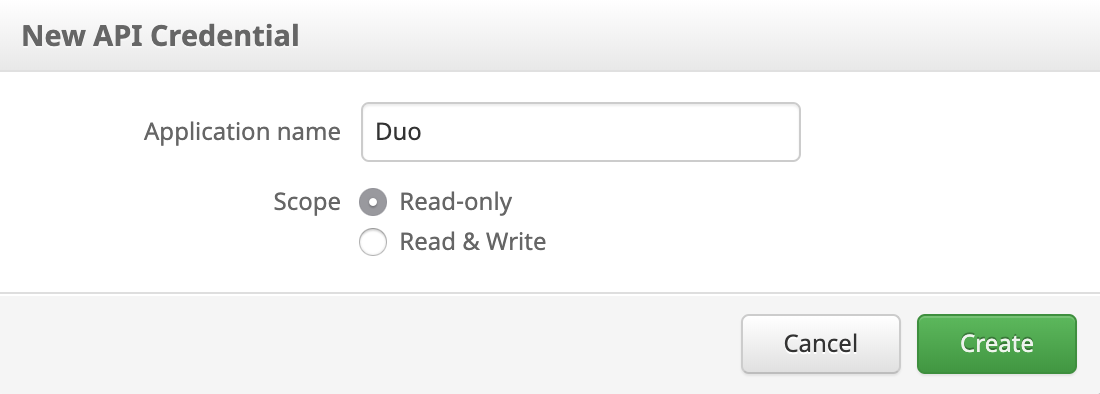
Click the New API Credential button, enter a name for the new API credential application (like "Duo"), and set the "Scope" to Read-only. Click Create when done.
-
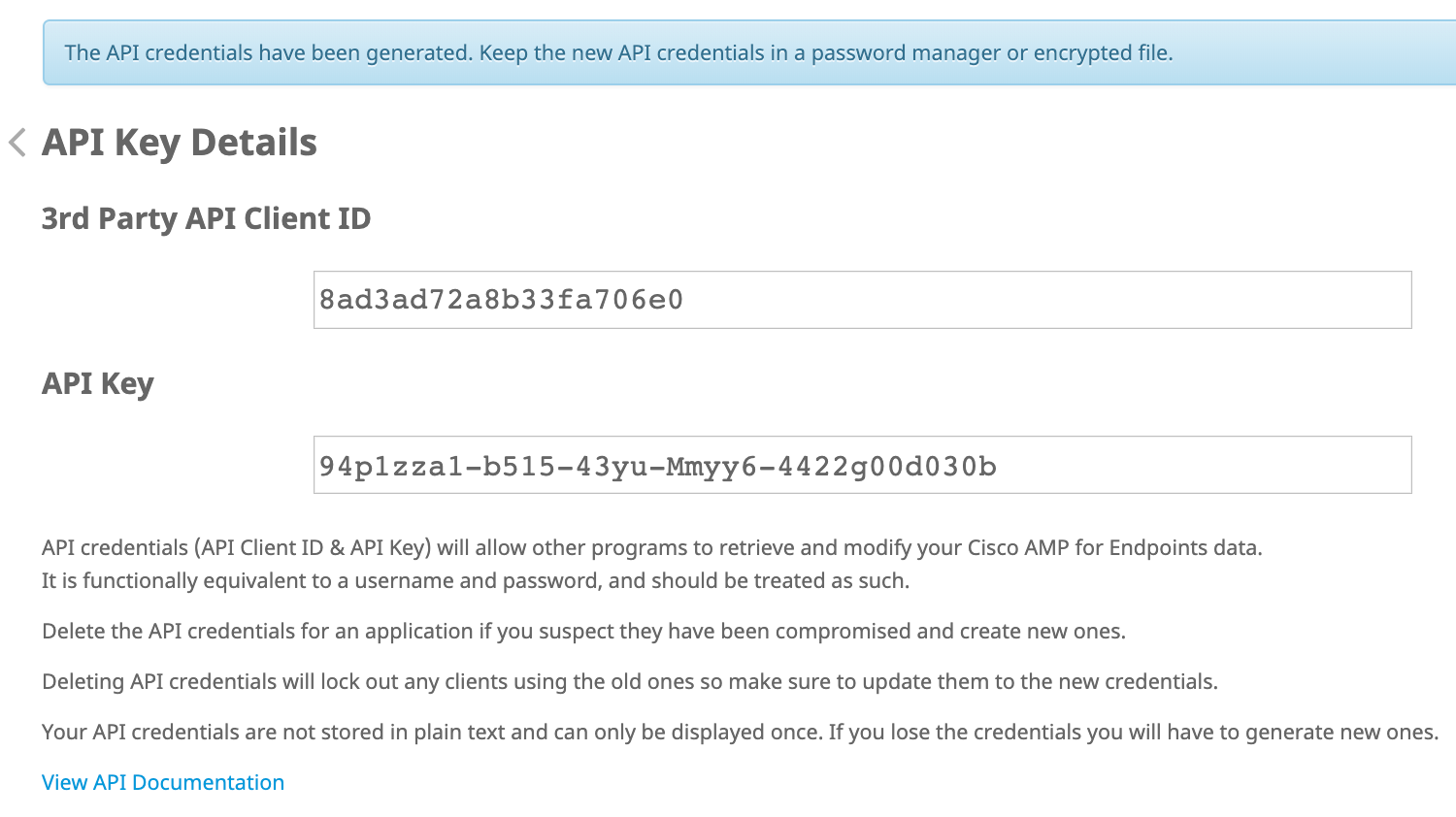
You'll see the API key details for the new credential you just created. Do not navigate away from this page before completing the rest of the Cisco Secure Endpoint integration configuration in Duo. If you leave this page without saving the API key to enter in Duo, you may not view it again and will need to delete this API credential and create a new one to continue.
-
Return to your Cisco Secure Endpoint integration page in the Duo Admin Panel.
-
Copy the 3rd Party API Client ID from the Cisco Secure Endpoint console and paste this in Duo as the Client ID value in the "Enter Cisco Secure Endpoint Credentials" section.
-
Copy the API Key from the Cisco Secure Endpoint console and paste this in Duo as the API Key value in the "Enter Cisco Secure Endpoint Credentials" section.
-
Click the Test Integration button. If the provided API information is correct, the "Hostname" information automatically populates.
-
Click Save Integration to complete the Cisco Secure Endpoint configuration.
-
Toggle the integration status to Enabled in the "Enable Cisco Secure Endpoint Integration" section to start using this integration.
Configure the Cisco Secure Endpoint Policy
Once you've configured the Cisco Secure Endpoint integration, you can configure the Trusted Endpoints policy to start blocking compromised endpoints as users authenticate to Duo-protected services and applications. Your client devices must be identified as trusted endpoints in Duo in order for Duo to utilize Cisco Secure Endpoint compromise information to permit or deny access to applications. Duo uses identifiers from the Duo certificate present on trusted endpoints or reported by Duo Desktop to match devices in Cisco Secure Endpoint and check their state.
-
Determine if you want to enable Cisco Secure Endpoint in the global policy or as a custom policy applied to specific applications (or select groups of users accessing specific applications). Review the Duo policy documentation to learn more.
-
When editing or creating the Duo policy to which you want to add Cisco Secure Endpoint verification, click Trusted Endpoints on the left side of the policy editor.
-
Ensure that Require endpoints to be trusted is selected and click the Allow Cisco Secure Endpoint to block compromised endpoints checkbox, and then save the policy.
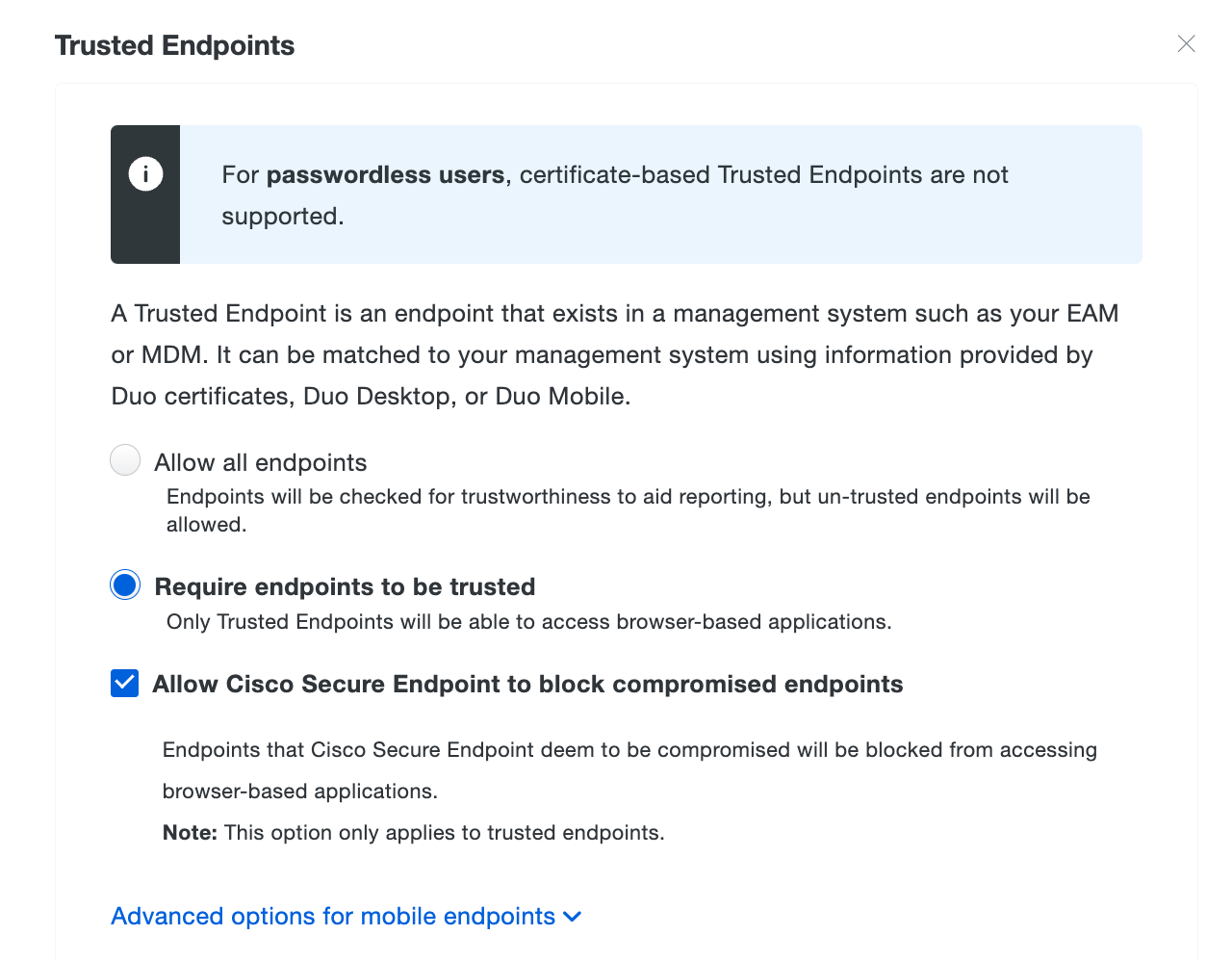
With the Cisco Secure Endpoint blocking policy setting enabled, Duo determines application access for Windows and macOS clients as follows:
|
Trusted Endpoints policy: Require endpoints to be trusted |
Trusted Endpoints policy: Allow all endpoints |
|
|
Cisco Secure Endpoint device status: Compromised |
Application access blocked ** | Application access allowed |
|
Cisco Secure Endpoint device status: Not compromised |
Application access allowed if device is trusted | Application access allowed |
Verify Your Setup
Once the above option is enabled for a Duo policy and an end-user attempts access to the associated application or is part of a user group from a compromised endpoint their request should be blocked and they will see an error message.
Troubleshooting
Need some help? Take a look at our Trusted Endpoints Knowledge Base articles or Community discussions. For further assistance, contact Support.
