Strengths and Weaknesses of MFA Methods Against Cyber Attacks: Part 2
The choice of which authentication methods to use is individual to every organization, but it must be informed by a clear understanding of how these methods defend against common identity threats.
In the first part of this three-part blog series, we discussed the various methods available to MFA users. In this part, we’ll evaluate each method’s effectiveness in defending against five common types of cyber-attack. The table below summarizes the findings.
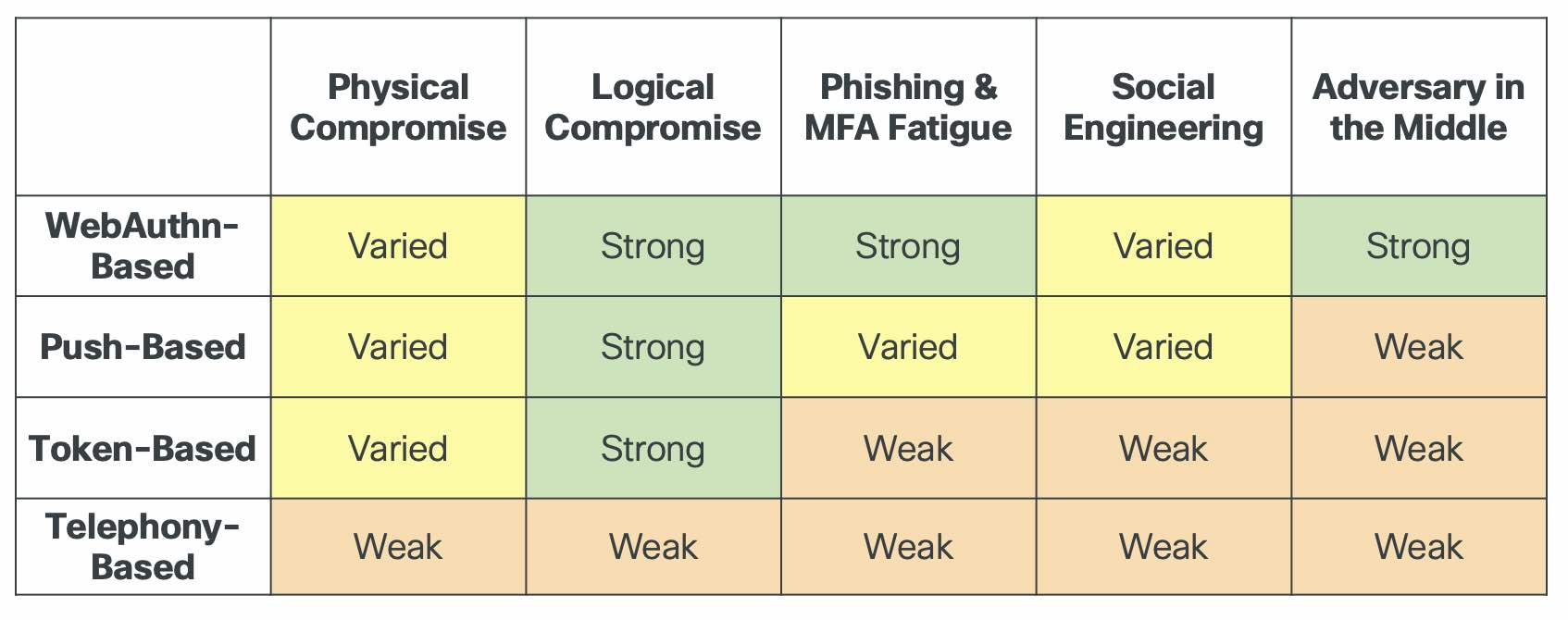
How MFA methods stand up to threats
Threat type #1: Physical compromise
Many authentication methods use device possession as a factor (i.e., evidence of a user’s identity), making physical security a concern. Devices can be stolen or temporarily accessed by an attacker to subvert MFA.
Varied protection: WebAuthn-based authentication, push-based authentication, token-based authentication
When used by WebAuthn-based authenticators, biometric user verification provides a strong layer of defense against physical compromise. However, some security keys do not support biometrics, while many authenticators fall back to passwords or passcodes when biometrics fail.
Physical security for push-based authentication relies on the access protections of the user’s phone. For best security, administrators should require that users implement screen lock on their devices when authenticating with Duo Mobile. They can additionally require biometric verification every time that a user approves a push.
Physical security of token-based authentication depends on the device. Some software tokens, like Duo Mobile, can be configured to require screen lock. However, many hardware tokens do not provide any protection. Furthermore, attackers with even temporary access to an HOTP device may memorize or write down a passcode and use it later. Users must take care to safeguard devices attached to keyrings and in other vulnerable locations.
Weak protection: telephony-based authentication
SMS passcodes and phone call authentication are vulnerable to physical compromise because text messages and phone calls often may be received without unlocking a phone. While users can elect secure screen lock settings, administrators cannot easily require them to do so.
Threat type #2: Logical compromise
Attackers may sometimes take virtual possession of authenticators without gaining physical access to a device. For example, by gaining access to a cryptographic key or taking possession of a phone number, they may be able to emulate the behavior of an authentication device.
Strong protection: WebAuthn-based authentication, push-based authentication, token-based authentication
While key theft is possible for these methods, most devices provide strong protections. WebAuthn-based authenticators use private keys that are not shared publicly and that can be stored securely on tamper-resistant hardware protected with strong encryption. Platform credentials (passkeys) that are synced using services like iCloud Keychain are encrypted in transit.
Duo’s push-based authentication uses private keys that are stored in encrypted form and never leave the device. Default Duo policy further prevents exfiltration of keys from Duo Mobile by requiring that user devices are not rooted or jailbroken.
Token-based authenticators use a secret key, called a seed, to generate passcodes. These seeds are encrypted when stored on both the device and on Duo servers.
Weak protection: telephony-based authentication
SIM swapping is a common technique that allows attackers to subvert telephony protections without physically stealing a phone. An attacker calls the phone carrier posing as the legitimate user and has the user’s phone number transferred to their own device. Then, they can authenticate via SMS passcode or phone call.
Threat type #3: Phishing and MFA fatigue
Phishing attacks and MFA fatigue attacks are related threats in which a user is given a fraudulent prompt to authenticate. In phishing, the attacker directs the user to a fake website with a login prompt that collects their password and/or single-use passcode. In an MFA fatigue attack, also known as push phishing or push harassment, the attacker uses stolen credentials to send the user repeated push requests in hopes that the user will inadvertently approve one.
Strong protection: WebAuthn-based authentication
WebAuthn-based authentication is sometimes referred to as “phish-proof” because it eliminates the need for shared codes, removing the risk that those codes could be intercepted. The browser also tells the authenticator what site the user is on, so credentials can only be used on the site they were created for. Authentications are verified locally on the login device, so the attacker cannot enlist the user’s help remotely in their authentication attempt via an MFA fatigue attack.
Varied protection: push-based authentication
Push-based authentication is vulnerable to MFA fatigue attack, but this threat can be mitigated through the use of numeric code matching, as in Verified Duo Push. Because the numeric code must be entered by the user, there is no risk of the attacker phishing the code (though other forms of social engineering are possible, see below). Admins can require that codes be entered for all push-based authentications, or they can use an approach like Duo Risk Based Authentication in which only risky authentications require the code.
Weak protection: token-based authentication, telephony-based authentication
Token-based and SMS passcode methods are vulnerable to passcode phishing, though the risk can partially be mitigated by adoption of TOTP rather than HOTP based tokens. Phone call authentication is vulnerable to MFA fatigue attacks.
Threat type #4: Social engineering
Social engineering is a class of techniques in which the attacker manipulates the legitimate user into aiding them in the attack. While phishing and MFA fatigue may be considered examples of social engineering, they are not the only ways that user behavior can be manipulated. For example, attackers will sometimes pose as fellow employees or IT team members to convince users to follow directions. Social engineering is often preceded by reconnaissance on professional social networks to make the engagements more personal and believable.
Varied protection: WebAuthn-based authentication, push-based authentication
While WebAuthn-based authentication is typically considered a strong protection against social engineering, the recent trend on many operating systems toward synced passkeys has opened the door to passkey sharing attacks. If a legitimate user is convinced to share their passkey, then the attacker can use the passkey on their own system. Biometric requirements do not mitigate this threat because once a passkey is stolen, it may be used by the attacker with their own biometric. Fortunately, many platforms implement additional measures to secure passkeys, such as requiring that sharing happens between devices in physical proximity.
Use of a numeric code with push-based authentication helps guard against MFA fatigue and passcode phishing attacks, but it does not close the door to other types of social engineering. An attacker can attempt to log in using a stolen password, then send the numeric code to the legitimate user and convince them to enter the code and confirm the push.
Weak protection: token-based authentication, telephony-based authentication
Token-based and telephony methods are subject to a wide array of social engineering techniques in which users are convinced to share a physical device, transfer a phone number, or enter a code.
Threat type #5: Adversary in the Middle
Adversary in the Middle (AiTM) is a sophisticated attack in which the attacker establishes a proxy server between the legitimate user and their login destination, allowing the attacker to steal credentials and cookies during an authentication attempt. Because the login is proxied to the legitimate destination, the user may be unaware that the attack is happening, while the adversary gains full access to the account.
Strong protection: WebAuthn-based authentication
WebAuthn-based authenticators protect uniquely against AiTM attacks. WebAuthn verifies the identity of the login site (e.g. duosecurity.com) and therefore will not work via a proxy connection. This property, known as origin binding, contributes to WebAuthn’s status as a “gold standard for MFA.”
Weak protection: push-based authentication, token-based authentication, telephony-based authentication
All these methods are vulnerable to AiTM attack. Even when second-factor authentication is out-of-band with the login, as in a push, the delivery of the session cookie can still be intercepted by the proxy.
What’s next
Understanding the threats affecting MFA is important, but the choice of authentication methods also depends on factors like cost and ease of use. In the next blog in this series, we’ll discuss how organizations can choose the methods that best suit their needs.

