Remote Desktop Threats & Remediations
Remote Desktop Protocol (RDP) enables much of today’s hybrid workforce, allowing employees to remotely access desktop computers regardless of their location. Like any remote access tool, however, it is susceptible to security threats, including brute force attacks.
Attackers can gain unauthorized access to an RDP connection via several brute force methods, the most common of which is credential spraying. In this attack method, a small number of commonly used passwords are tried over many user accounts in succession. Many free and open-source tools, including NLBrute, Crowbar and Hydra, currently exist to allow attackers to automate these efforts over many user accounts at once. Once access is gained, even to a single user account, the results can be devastating. Malicious actors can potentially access any files on the desktop, install and operate malware, exfiltrate user and customer data, and access other devices on the same network. Research by Sophos estimates that 95% of all attacks in the first half of 2023 involved RDP access and emphasizes taking steps to further secure RDP applications.
"Research by Sophos estimates that 95% of all attacks in the first half of 2023 involved RDP access."
While securing RDP applications with multi-factor authentication (MFA) is an essential first step, we have seen a recent uptick in large-scale RDP attacks that can successfully subvert traditional MFA depending on the account policies and configuration. We will detail how these attacks appear in Cisco Duo authentication data, as well as outline simple and practical steps that you as an administrator can take to configure Duo to prevent this type of attack from infiltrating your environment.
Identifying RDP Brute Force attacks in MFA logs
As part of ongoing threat hunting efforts in collaboration with Cisco Talos Intelligence Group, we on Duo’s Security Data Science team sought to identify IP addresses that were responsible for RDP attack attempts on Duo customers. Over authentication data from 2023, we analyzed any IPs meeting the conditions of at least 100 authentication attempts to RDP applications over at least 3 organizations deploying Duo, with at least a 70% rate of failure. After vetting these IP addresses with the assistance of Talos, we identified 52 IP addresses confirmed or highly likely to be associated with RDP brute force attack patterns.
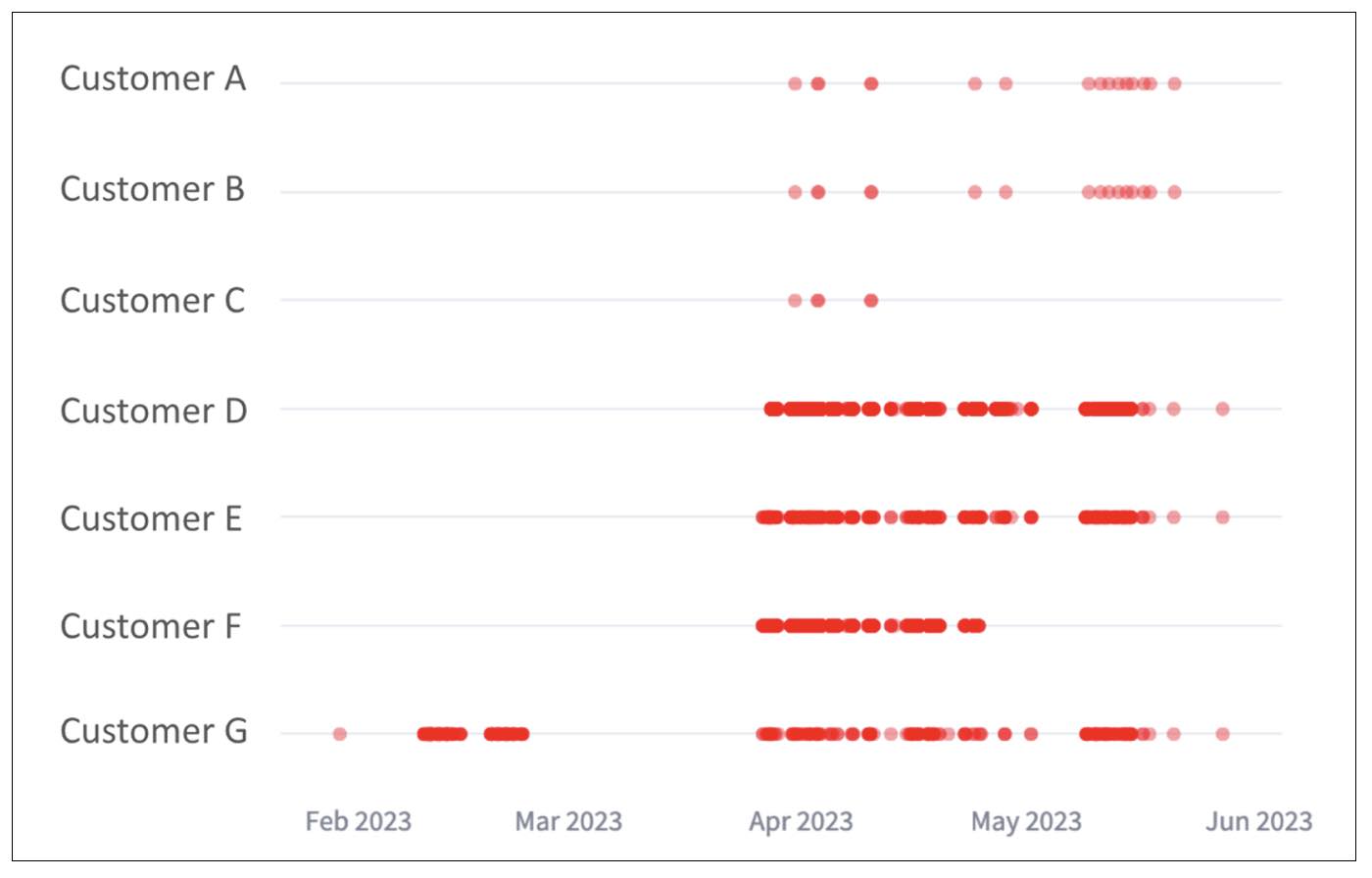
Observed behavior from one such IP can be seen below, with the vertical axis representing individual customers. With this visualization, we can see the attackers crawling customer environments, sending repeated failed attempts to a group of customer networks. All attempts shown here are failures. (Note that this is only a sample of the impacted customers).
The individual IPs and their corresponding active protocols varied widely, as we observed using Censys Search. Of the 25 hosts with active protocols at the time of our hunting efforts, 15 were running file-sharing protocols such as SMB and FTP, indicating file exfiltration as a possible primary goal of these attacks. The remaining active hosts were running a variety of VPN protocols, including OpenVPN, IKE (IPSec), and PPTP, likely in an attempt to obfuscate the true source of the attacks.
Most hosts belonged to cloud hosting providers, the most common being the Panamanian provider “Flyservers”. A small number of hosts appeared to be residential or commercial hosts that had been captured by the attackers and used to send malicious requests.
Duo has since added all IPs suspected of RDP brute force attacks to our global block list, preventing them from any further access to our service across all Duo customers. As it is trivial, however, for attackers to rotate IP addresses, we will outline ways in which long term prevention can be achieved through improved security posture and policy configurations.
Prevention
Deny unenrolled users
Among the roughly 80,000 attempts from these RDP brute force networks, only 2% of authentications were successful. Many of these successes were potentially preventable via policy configurations within the Duo Admin Panel. The first of these relates to the way that new users enroll in Duo, particularly the ability to allow unenrolled users (those without any user account in Duo) to bypass MFA upon initial access. Of the successful accesses by the attackers in this case, 53% were to user accounts which had this MFA bypass policy configured. By contrast, over half of all malicious attempts were stopped via denying access to users not enrolled in Duo.
If possible, we recommend the following prevention measures to reduce the attack surface area.
Good
Enable monitoring on authentication logs to be notified when access to an application occurs as a result of allowing unenrolled users, particularly upon access to RDP applications. Repeated successes from a single IP address with no further user enrollment following the authentication may indicate an RDP attack and that user credentials have been compromised.
Better
Deny unenrolled users access to RDP applications by setting a per-application policy. Unenrolled users can still be allowed to enroll via other applications you have configured, just not through RDP applications for which access can be easily automated by attackers.
Best
Deny all access to unenrolled users and enroll users in Duo MFA via either automatic enrollment or a manual user import.
User lockout mechanisms
For users enrolled in MFA, there is still a risk of RDP account access by an attacker. The most common attack pattern seen against enrolled users were methods known as push harassment (in which a single user is sent many push attempts in the hopes that they will eventually accept) or push spraying (in which push attempts are sent across many users). A visual example of this is shown below, in which a user was repeatedly sent push requests from an RDP attack IP until they accepted.
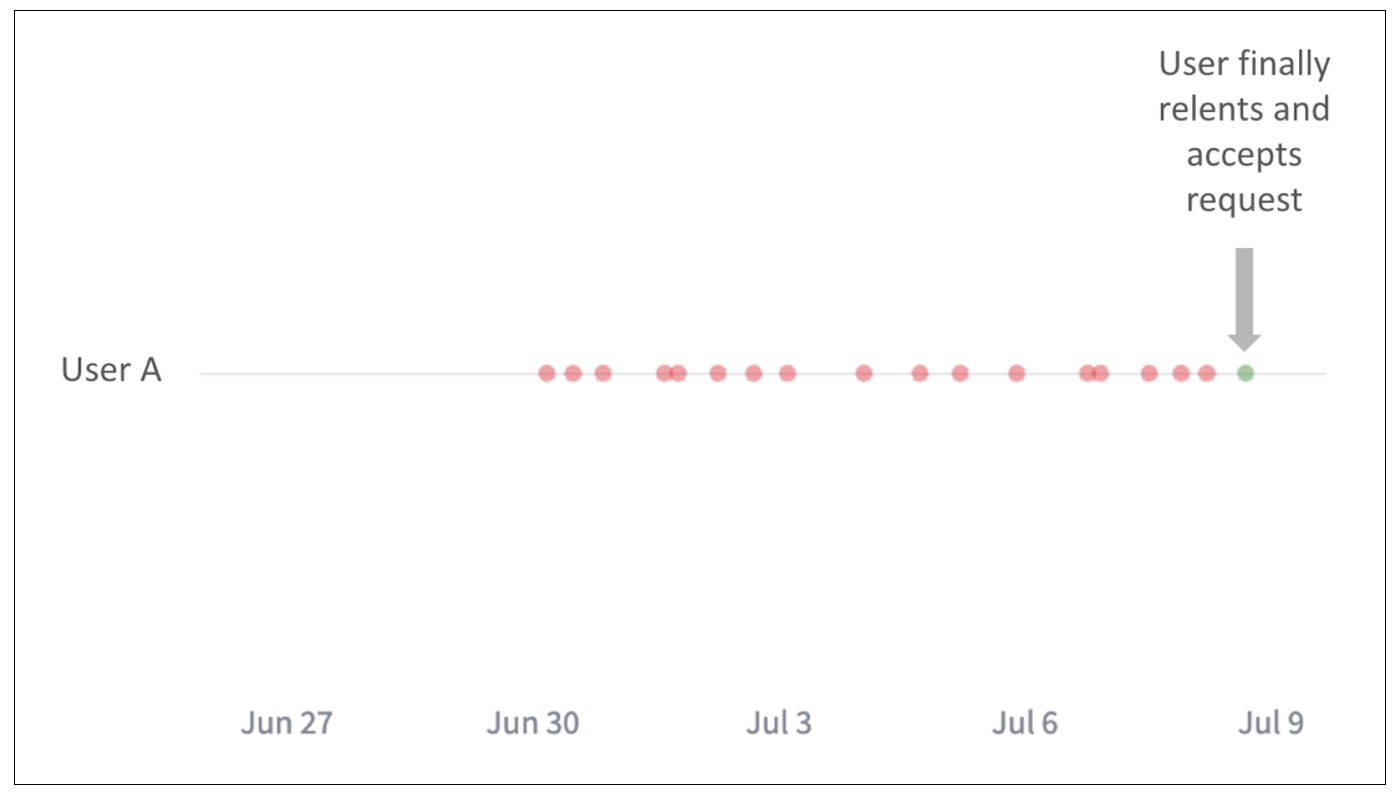
One way of preventing a malicious actor from sending repeated pushes to a user is by enabling a lockout threshold in the Duo Admin Panel. Roughly 11% of recent RDP brute force attempts from the IPs analyzed were prevented by user lockout mechanisms, the majority of which having a threshold of 10 repeated failures before locking out a user. 10 is the default number of failures before a user’s account is locked out, however, a more aggressive threshold can be customized in your Duo Admin Panel.
For increased visibility, administrators can configure Duo to notify them in the instance that a user is locked out, to further monitor suspicious activity. If this occurs, and users cannot account for the repeated failures, this may indicate user credential compromise.
User location restriction
To prevent malicious requests from reaching users in the first place, admins should configure Duo to block requests from countries that they do not expect to see traffic from. Of the IPs studied in these attacks, they originated from countries including Iran, Russia, Hong Kong, the Netherlands, Ukraine, Estonia, Romania, Pakistan and Nicaragua, all of which accounted for less than 1% of the benign traffic of the impacted customers. If it is conducive to your organization’s setup, consider denying access or limiting available authentication factors for requests that originate somewhere other than your organization’s expected locations.
Users that live in countries atypical to the majority of an organization’s users or who may need occasional access from a country that is otherwise blocked can be added to a user group with a specific policy exemption if necessary.
Summary
Basic MFA is a necessary first step in securing RDP applications. Without proper configuration, however, it’s still possible for attackers to subvert security measures and gain access to critical data and infrastructure. While attacks are constantly evolving, taking essential steps such as blocking unenrolled access and enabling user lockout functionality on RDP applications can help to prevent users from receiving malicious requests.

