New Duo E-Book, Attack Vectors Decoded: Securing Organizations Against Identity-Based Threats
Identity-based cyberattacks are a challenge across all organizations, regardless of size, industry or technology. And every time organizations put up a new defense, cybercriminals seem to find their way around it. This becomes a constant cycle of organizations introducing new protections and attackers finding ways to exploit them.
Recently, attackers have targeted multi-factor authentication (MFA). MFA is a common second line of defense against compromised passwords. Even if an attacker has access to a username and password, they still need access to the second authentication factor to break into the organization.
However, attackers are finding ways around MFA. They can take advantage of the less secure methods of authentication, like one-time passcodes, and socially engineer a user to hand over codes or intercept them before they reach the end user. They can engage in MFA fatigue attacks where a trusted user might absentmindedly accept a push request because they’re so used to doing it or might accept the push requests to get the endless notifications to stop.
While attackers are finding new and creative ways to victimize users, organizations can deploy many tools to protect against these types of attacks. In Duo’s new eBook Attack Vectors Decoded: Securing Organizations Against Identity-Based Threats, we summarize the top attack vectors targeting users and what organizations can do fortify their defenses.
So, what can organizations do to better protect themselves? Some of the solutions are easy policy changes that organizations can turn on immediately, like Duo’s Risk-Based Authentication (RBA). RBA analyzes risk signals at the point of login and can remove barriers for trusted users, while requiring more secure factors when new risk is identified (like multiple denied push requests being sent to the same user).
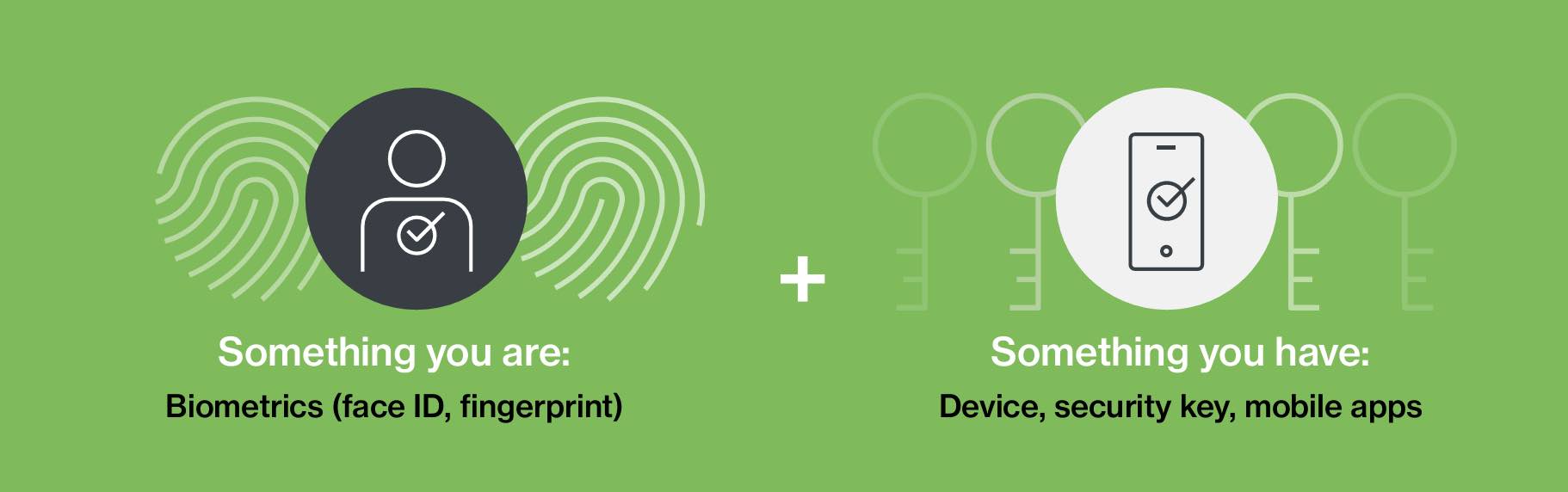
Other solutions are more of a journey, like rolling out passwordless across your organization. Passwordless login removes the “something you know” (e.g., the password) from the login process and instead uses “something you are” (e.g., a biometric) and “something you have” (e.g., a device). A user accesses an application with an asymmetric key exchange — a public key (that is held by the application), unlocks a private key that is secured on the device (so it cannot be stolen). While passwordless offers a phishing-proof solution, there are requirements to deployment, like ensuring all users have access to a biometric on their device or a security key.
And finally, organizations can combine a risk-based and phishing-proof authentication approach with device trust policies, like Duo’s Trusted Endpoints. Trusted Endpoints enables an organization to only let in managed or known devices so fraudulent MFA requests on an unknown device never even reach the end user.
To learn more about the current identity-focused attacks and how you can better protect your organization today and in the future, be sure to read Attack Vectors Decoded: Securing Organizations Against Identity-Based Threats today.
If you’re interested in a deeper dive into this topic, also check out our new Duo labs piece that provides detailed, research-backed insight into identity threats and how to protect against them.

