Documentation
Duo Two-Factor Authentication for OpenVPN Access Server
Last Updated: April 20th, 2022Contents
These instructions will enable you to add Duo two-factor authentication to an OpenVPN Access Server installation. If you wish to use Duo with the OpenVPN Community Open Source Software Project, refer to the OpenVPN instructions instead.
Duo 2FA for OpenVPN AS doesn't support inline self-service enrollment for new Duo users. We recommend using bulk enrollment to send your users unique self-enrollment links via email. Read the enrollment documentation to learn more.
If using the OpenVPN client for incoming connections, ensure your users have version 2.2 or later.
This application communicates with Duo's service on SSL TCP port 443.
Firewall configurations that restrict outbound access to Duo's service with rules using destination IP addresses or IP address ranges aren't recommended, since these may change over time to maintain our service's high availability. If your organization requires IP-based rules, please review Duo Knowledge Base article 1337.
Effective June 30, 2023, Duo no longer supports TLS 1.0 or 1.1 connections or insecure TLS/SSL cipher suites. See Duo Knowledge Base article 7546 for additional guidance.
First Steps
Before moving on to the deployment steps, it's a good idea to familiarize yourself with Duo administration concepts and features like options for applications, available methods for enrolling Duo users, and Duo policy settings and how to apply them. See all Duo Administrator documentation.
To get started securing your OpenVPN Access Server with Duo, you'll need to:
- Sign up for a Duo account.
- Log in to the Duo Admin Panel and navigate to Applications.
- Click Protect an Application and locate the entry for OpenVPN Access Server in the applications list. Click Protect to the far-right to configure the application and get your integration key, secret key, and API hostname. You'll need this information to complete your setup. See Protecting Applications for more information about protecting applications in Duo and additional application options.
- Download the latest duo_openvpn_as release package as a zip file from GitHub and uncompress the package on your OpenVPN AS server.
The security of your Duo application is tied to the security of your secret key (skey). Secure it as you would any sensitive credential. Don't share it with unauthorized individuals or email it to anyone under any circumstances!
Configure the Post-Auth Script
-
Extract the Duo OpenVPN Access Server plugin downloaded from Duo's GitHub repository if you haven't already done so.
-
Open the
duo_openvpn_as.pyscript in a text editor and fill in these required parameters where instructed:Key Required? Description IKEYRequired Your integration key, obtained from the details page for the OpenVPN AS application in the Duo Admin Panel. SKEYRequired Your secret key, obtained from the details page for the OpenVPN AS application in the Duo Admin Panel. HOSTRequired Your Duo API hostname (e.g. api-XXXXXXXX.duosecurity.com), obtained from the details page for the OpenVPN AS application in the Duo Admin Panel.# ------------------------------------------------------------------ # Fill in your integration credentials on the following three lines: IKEY = 'INTEGRATION_KEY' SKEY = 'SECRET_KEY' HOST = 'API_HOSTNAME' # ------------------------------------------------------------------ -
Move the
duo_openvpn_as.pyscript to the OpenVPN AS scripts folder - typically/usr/local/openvpn_as/scripts/- and make sure it is executable.$ mv duo_openvpn_as.py /usr/local/openvpn_as/scripts/ $ chmod a+x /usr/local/openvpn_as/scripts/duo_openvpn_as.py
Enable the Post-Auth Script
-
Use OpenVPN Access Server's command-line interface to set
duo_openvpn_as.pyas your post-auth script:$ /usr/local/openvpn_as/scripts/sacli -a admin_username -i -k auth.module.post_auth_script --value_file=/usr/local/openvpn_as/scripts/duo_openvpn_as.py ConfigPutWhere admin_username is the username of an administrator on your OpenVPN Access Server instance. You'll be prompted to enter the administrator account's password.
-
Restart the service to commit your configuration changes:
$ /usr/local/openvpn_as/scripts/sacli -a admin_username -i ResetWhere admin_username is the username of an administrator on your OpenVPN Access Server instance. You'll be prompted to enter the administrator account's password.
Test Your Setup
After you have enabled the Duo Post-Auth script, try to log in as a regular VPN user through the OpenVPN Access Server web interface. If you are using an account which has not previously been enrolled for Duo authentication, your login attempt will be denied with a self-enrollment URL. Visit the URL, enroll your phone, and then try logging in again.
You will only receive a self-enrollment URL if you log in to your OpenVPN Access Server instance with a web browser; this mechanism will not work with native clients (e.g. OpenVPN Connect). You can bulk enroll users if they won't be logging in through the web interface.
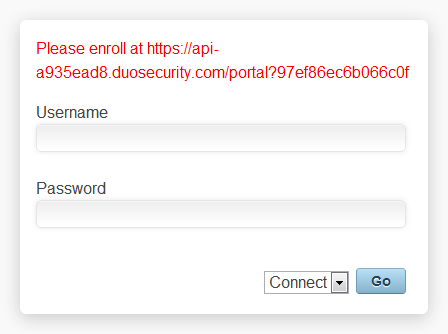
When you log in as a Duo-enrolled user, you will see a secondary prompt (either via a web browser or with a native client), with instructions to enter a Duo passcode (eg. "124356") or an alternate factor identifier:
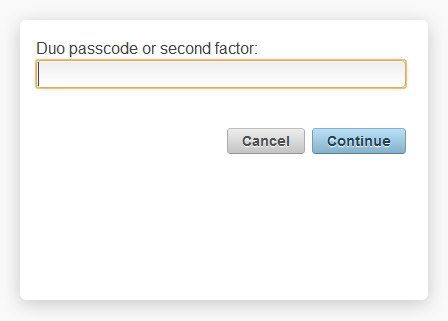
Choose from the following factors:
| push |
Perform Duo Push authentication You can use Duo Push if you've installed Duo Mobile and added your account to it |
| phone | Perform phone callback |
| sms |
Send a new batch of SMS passcodes Your authentication attempt will be denied. You can then authenticate with one of the newly-delivered passcodes. |
You can also specify a number after the factor name if you have more than one device enrolled. So you can enter phone2 or push2 if you have two phones enrolled.
If you enable the optional AUTOPUSH setting, no secondary Duo prompt is shown and instead the user receives an automatic Duo Push request or phone call to their default device. If the user has no device activated for use with Duo Mobile or no phone capable of receiving an incoming call from Duo, the user cannot login.
Troubleshooting
Need some help? Take a look at the OpenVPN AS Frequently Asked Questions (FAQ) page or try searching our OpenVPN AS Knowledge Base articles or Community discussions. For further assistance, contact Support.
Optional Settings
These optional settings may also be configured in the duo_openvpn_as.py script:
| Key | Required? | Description |
|---|---|---|
PROXY_HOST
|
Optional |
Use the specified HTTP proxy for the outbound request to Duo's service. No proxy used if not set. |
PROXY_PORT
|
Optional |
Use the specified HTTP proxy port for the outbound request to Duo's service. No effect if |
SKIP_DUO_ON_VPN_AUTH
|
Optional |
Do not perform Duo authentication for VPN client connections. Web interface logins still require 2FA. One of: |
AUTOPUSH
|
Optional |
Do not show Duo factor selection and automatically send a Duo Push request to the user. One of: |
Network Diagram
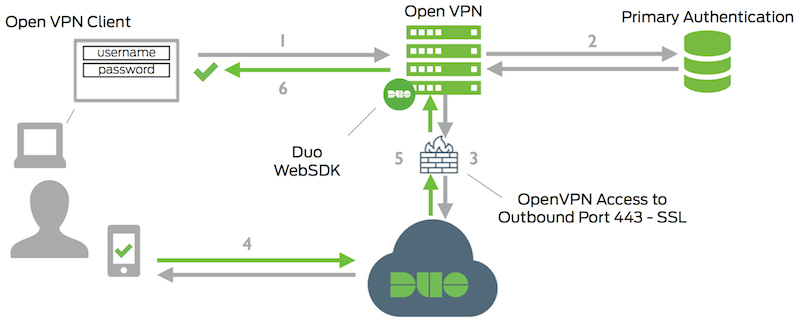
- Open VPN connection initiated
- Primary authentication
- Open VPN connection established to Duo Security over TCP port 443
- Secondary authentication via Duo Security’s service
- Open VPN receives authentication response
- Open VPN session logged in
