Blocking Authentication Attempts from Anonymous Networks
The Dark Web can hide criminals and other large-scale threat actors that may want to conduct illegal transactions. Now researchers are warning companies to check for illegal web traffic on their own corporate networks, since they might be unwittingly supporting anonymous networks that facilitate the Dark Web, such as Tor, as the Wall Street Journal reported.
Note: The Dark Web is not to be conflated with the meaning of the Deep Web. The Deep Web is a term for all sites on the web that can’t be reached by a search engine. The Dark Web is a smaller subset that hides the IP addresses of the servers that run them, by using Tor or other anonymous networks. This Wired article explains it well.
The Tor browser (originally named The Onion Router) is software that conceals a user’s Internet activity and location. There are many different use cases - journalists can use the browser to communicate more safely with whistleblowers. A branch of the U.S. Navy uses Tor for open source intelligence gathering. Activists and other individuals can also use Tor to communicate privately despite government surveillance.
But Tor users are often targeted by law enforcement. Most recently, it was revealed that the Federal Bureau of Investigation (FBI) was attempting to unmask the true IP address of a Tor user by sending him a malicious file, as the Hacker News reported. This was found among the one million internal emails between the surveillance software company Hacking Team and the FBI.
So how does it work? Tor is comprised of two parts - the software you can download that allows you to use the Internet anonymously, and the volunteer network of computers (nodes or relays) that supports the software.
Tor uses a set of randomly selected servers (relays) to build a path through each server to send you to the website you want to visit. Wrapping your request in three layers of encryption ensures that each server can only see certain bits of data content as it’s passed along from relay to relay. Learn more about Tor in Duo Tech Talks: Encryption Works: A Look at Tor and SecureDrop presented by Runa A. Sandvik.
According to an IBM report on the Dark Web, security researchers are concerned that companies may be unknowingly hosting relays for this anonymous network. Specifically, they warn against hosting exit nodes/relays on corporate networks, the final server that traffic passes through before reaching its final destination.
Exit nodes display the IP address of the server, revealing them as the source of the traffic. That means, if a malicious attack is delivered to another organization over the Tor network and your company is the exit node, you could get blamed for their attack.
Many Tor attacks are launched with the intent to steal intellectual property or spy on company operations, as could be inferred by the top industries targeted include information and communications companies, manufacturing and finance and insurance, according to IBM’s report.
There’s risk to your company as well if Tor exit nodes are communicating with your network - attackers could potentially bypass your security measures and steal your data by exploiting the default encryption capability of anonymous networks.
IBM recommends setting blocking rules for known exit nodes (by using publicly available lists of proxy nodes) into your firewall infrastructure to help deter anonymous-network attacks from your environment. But while firewalls can provide network security, controlling the flow of data in and out of your on-premises networks, what about your cloud/web-based applications and services? You still need to protect those.
There’s another way to ensure both on-premises and cloud app protection. Advanced authentication tools allow you to set up custom policies and controls that can further verify a user’s identity before he/she is granted access to your apps, based on certain criteria.
Using the Duo Access, data about your users’ authentication devices is aggregated and analyzed to give you insight into what kind of network they’re authenticating from. That’s some pretty useful data that you can, in turn, use to automatically block any auth attempts from any anonymous networks, such as Tor.
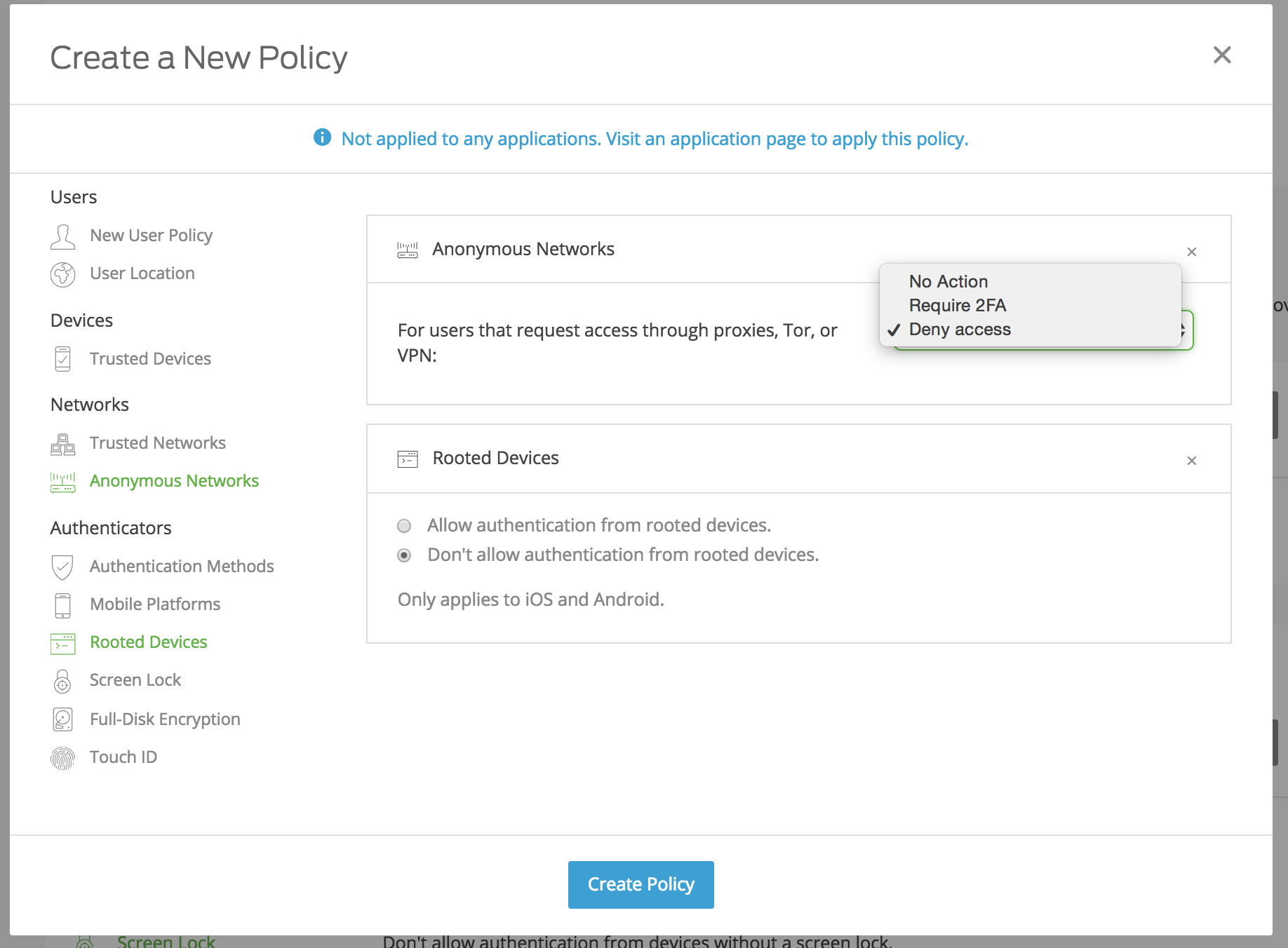
You can also block authentication attempts based on user location, type of device and OS, rooted/jailbroken status and more. Learn about other policy and controls you can use to protect your organization against threats associated with anonymous networks.